Customizing the Developer Portal and Gateway URLs for Tenants¶
The default URL of WSO2 API Manager Developer Portal (https://<HostName>:9443/devportal) and the gateway URLs (http://<HostName>:8280/t/<tenant-domain> and https://<HostName>:8243/t/<tenant-domain>) can be customized per tenant. Following steps illustrate how to configure devportal and gateway custom URLs for a given tenant.
Configure per tenant custom domain mappings¶
Note
Only the super tenant can add custom URLs in their registry space for other tenants. Tenants cannot configure custom URLs for their Developer Portal or Gateway.
-
Log in to the management console (
https://<HostName>:9443/carbon) as the super admin. -
In the Main menu, click Browse under Resources.

-
Navigate to the
/_system/governanceregistry path and createcustomurl/api-cloud/<tenant-domain>/urlMappingdirectory structure in the registry, as shown in the following diagram. Replace the<tenant-domain>placeholder with the domain name of the tenant you want to customize the devportal and gateway URLs. For details on how to create and manage multiple tenants, see Managing Tenants.
To create a directory in the registry path,
-
Navigate to the location in the registry browser, click and open the location.
-
Click Add Collection and specify the name of the directory and click Add.

Note
In API Cloud, this directory structure is created automatically when specifying the custom URL through the UI.
-
-
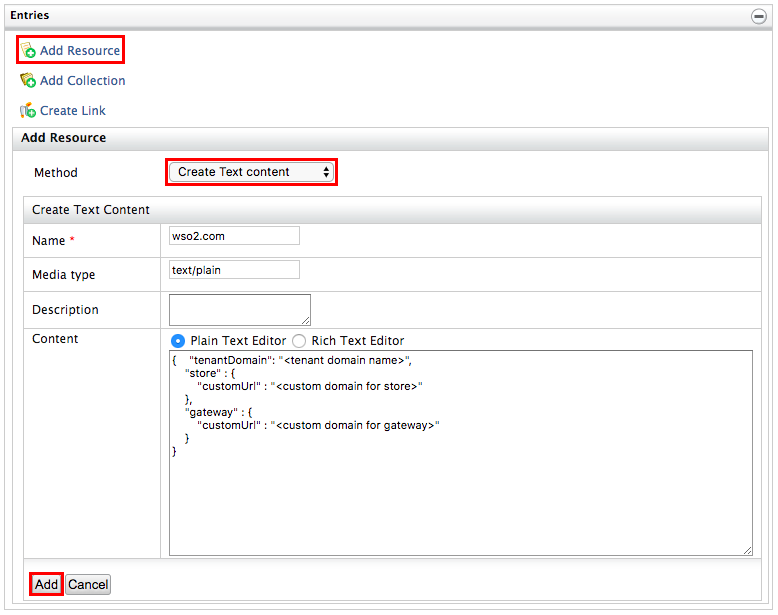
Navigate to
/_system/governance/customurl/api-cloud/<tenant-domain>/urlMappingin the registry. Click Add Resource under Entries and select Create Text Content as the resource type. -
Provide tenant domain as the resource name and add the following configurations as the resource content. In here, you need to specify the developer portal and the gateway custom URLs for the respective tenant.
Configure per tenant service provider creation for the Developer Portal¶
By default the developer portal is acting as SAAS app, which is shared among all the tenants. But when custom URLs are enabled for a given tenant, this particular SAAS application cannot be used(Due to custom callback URLs) for tenant login management. Hence, below steps has to be followed in order to enable service provider creation per tenant.
-
Carry out the steps provided in the Advanced Configurations section.
-
Edit the Advanced Configurations and add following new property to enable per tenant service provider creation for the respective tenant. Save the content.

Configure the load balancer for custom URLs¶
Carry out the following steps to configure NGINX as the load balancer to support custom tenant URLs.
Note
Although the following section instructs you to use NGINX as the load balancer, you can use any load balancer in your deployment based on your preference.
-
Install NGINX. For more information on installing NGINX, refer NGINX official documentation.
-
Navigate to the
<API-M_HOME>/repository/resources/securitydirectory and use the following command to add the Nginx certificate to the client trust store. -
Add following Nginx server configurations to handle customized developer portal URL configured for the tenant.
server{ listen 443; ssl on; server_name "{custom-url-for-dev-portal}"; ssl_certificate {nginx-certificate-file-path}; ssl_certificate_key {nginx-key-file-path}; location /{ proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://{server-IP}:9443/devportal/; proxy_redirect https://{server-IP}:9443/devportal/ /; proxy_set_header X-WSO2-Tenant "{tenant-domain}"; } location ~ (/api/am/devportal/v3|/authenticationendpoint|/logincontext|/commonauth|/oidc) { proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://{server-IP}:9443; proxy_set_header X-WSO2-Tenant "{tenant-domain}"; } location ~ (/oauth2) { proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://{server-IP}:9443; proxy_redirect {server-hostname-configured-in-toml-file}/ {custom-url-for-dev-portal}/; proxy_set_header X-WSO2-Tenant "{tenant-domain}"; } }server{ listen 443 ssl; server_name developer.wso2.com; ssl_certificate /usr/local/etc/nginx/ssl/test.crt; ssl_certificate_key /usr/local/etc/nginx/ssl/test.key; location /{ proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://192.168.1.8:9443/devportal/; proxy_redirect https://192.168.1.8:9443/devportal/ /; proxy_set_header X-WSO2-Tenant "wso2.com"; } location ~ (/api/am/devportal/v3|/authenticationendpoint|/logincontext|/commonauth|/oidc) { proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://192.168.1.8:9443; proxy_set_header X-WSO2-Tenant "wso2.com"; } location ~ (/oauth2) { proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://192.168.1.8:9443; proxy_redirect https://192.168.1.8:9443/ https://developer.wso2.com/; proxy_set_header X-WSO2-Tenant "wso2.com"; } } -
Add following Nginx server configurations to handle customized Gateway URL configured for the tenant.
server{ listen 443; ssl on; server_name "{custom-url-for-gateway}"; ssl_certificate {nginx-certificate-file-path}; ssl_certificate_key {nginx-key-file-path}; location /{ proxy_set_header X-Forwarded-Host $host; proxy_set_header X-Forwarded-Server $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; proxy_read_timeout 5m; proxy_send_timeout 5m; proxy_pass https://{server-IP}:8243/t/{tenant-domain}/; } }
Note
When adding the customUrl parameter, make sure to add the valid context that the Developer Portal is accessed from.
- Add the server name provided for the devportal in the nginx configurations to the callback URL of apim:devportal service provider. === "Format"
Note
When adding the devportal URl to the callback URL regex, make sure to append it without removing the localhost:9443.
-
Add the following idp configurations to the
deployment.tomlfile to make devportal login when accessing from the publisher portal.
Now you should be able to access the developer portal and the gateways using custom URLs defined.