Multiple Key Manager Support in WSO2 API Manager¶
WSO2 API Manager provides an admin functionality for admins/tenant admins to configure different authorization servers as Key Managers. This brings the capability of supporting multiple Key Managers for a given API.
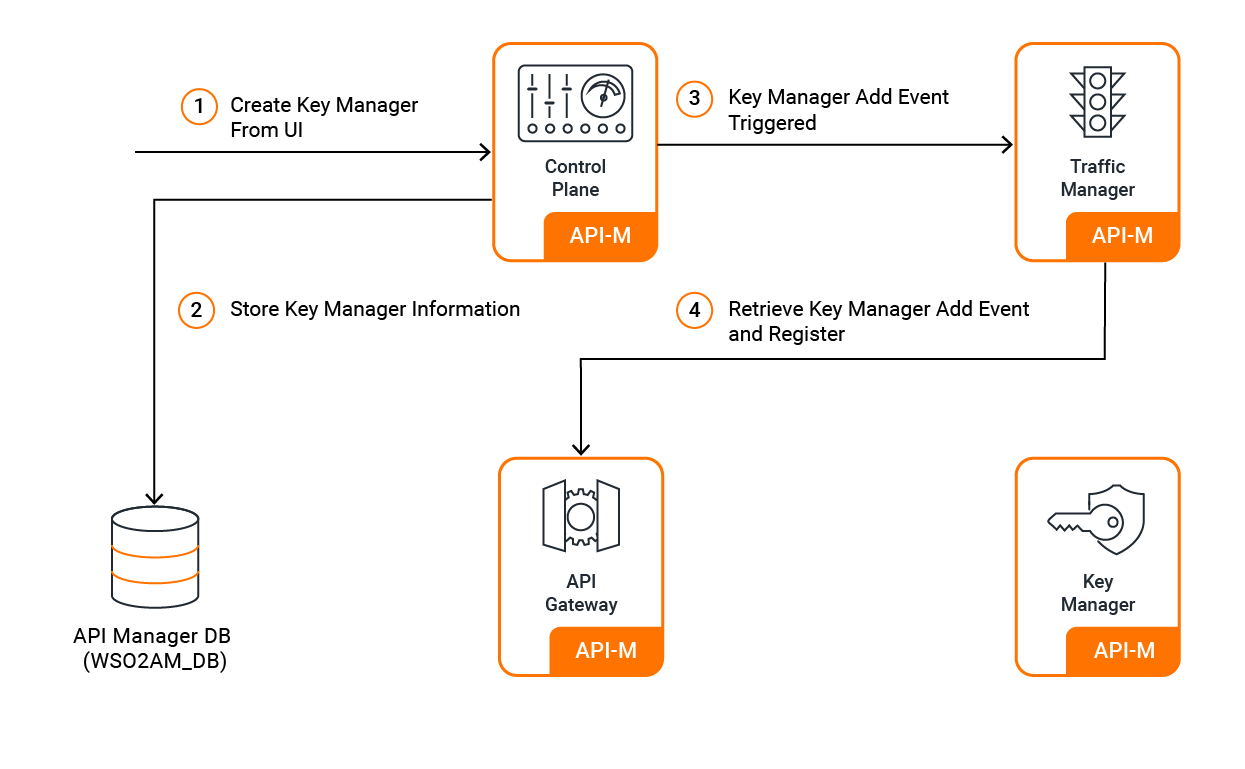
When a Key Manager is added via the Admin Portal, it is persisted in the APIM DB as well as an event is triggered to the Traffic Manager. As a result, the Gateway will receive the event and register the Key Manager in the Gateway. Therefore, the Key Manager will be registered as another Key Manager and it will be available for the APIs that are created within the tenant.
The Key Manager configuration initialization at server startup takes place through an internal API. However, the UI components in Publisher, developer Portal, and Admin Portals populate Key Manager details from the database.
When generating keys for a selected Key Manager, it checks if the Key Manager configurations have the consumer app creation enabled. If it is enabled, it generates the consumer App upon validation of the required parameters.
Token validation¶
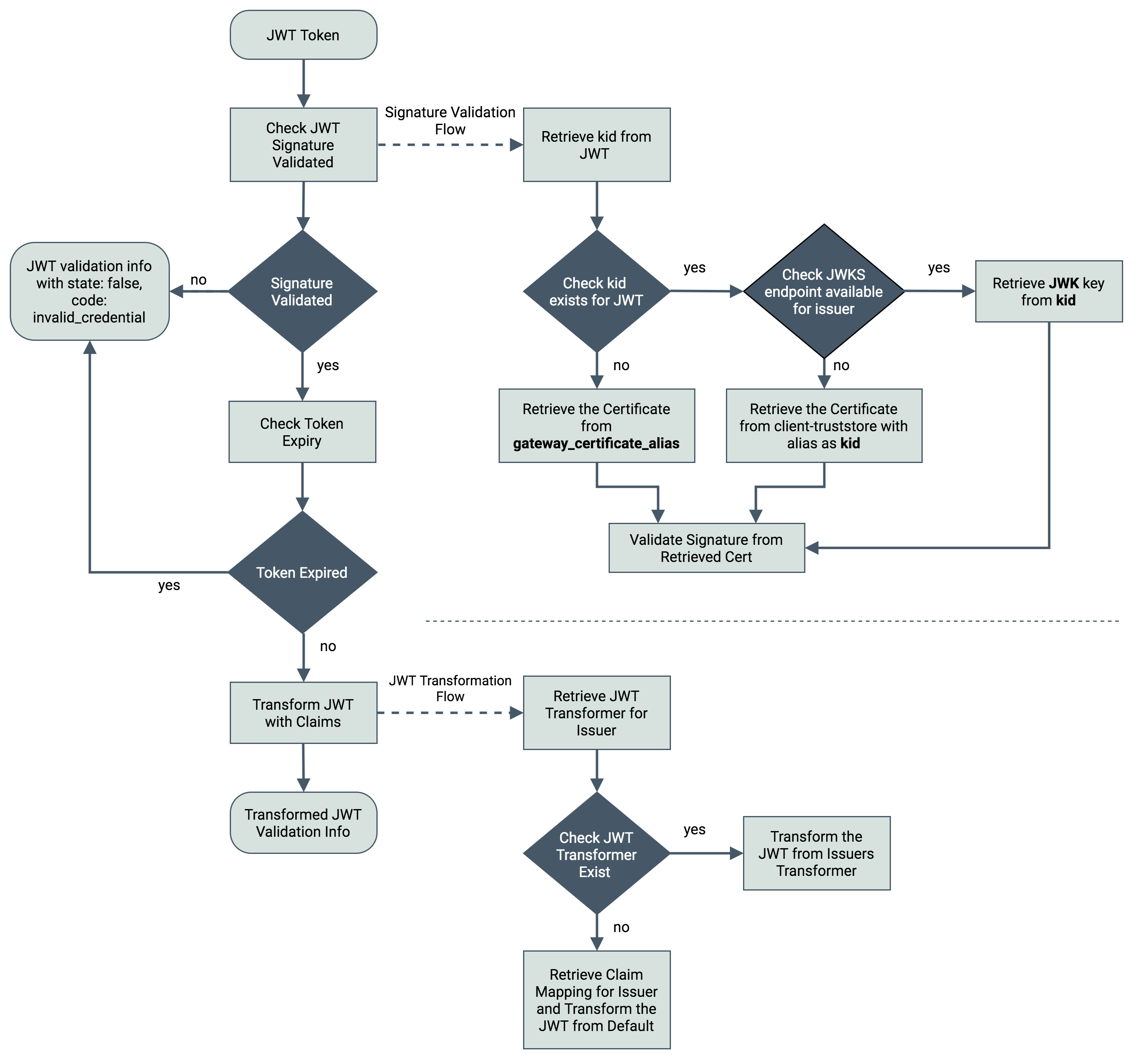
If the token is a JWT token, it retrieves the Issuer details from the JWT and obtains the relevant Key Manager. If the Key Manager is not enabled for the API, token validation fails. If the Key Manager is enabled, the token is validated through the JWT validator.
For non JWT tokens, the token is validated based on the token handling options provided in the Key Manager configurations of the intended Key Manager.
After token validation takes place by retrieving the consumer key, subscription validation takes place at the Gateway.
If the subscription validation is successful, the scope validation takes place.
Finally if the backend JWT generation is enabled, it generates the JWT.
Role-Based Key Manager Restriction¶
Access to Key Managers can be restricted based on user roles from the admin portal.
When the permission type for the role-based restriction is set to ALLOW, only users with the specified roles are permitted to use the key manager for key generation.
When the permission type for the role-based restriction is set to DENY, users with the specified roles are not allowed to use the key manager for key generation.
Note
- When implementing role-based access restrictions, it is important for administrators to exercise caution and be mindful of potential scenarios where users, may not have visibility or access to key managers. Kindly be cautious when restricting key managers.
- A Key Manager can possess either a whitelist or a blacklist, but not both simultaneously.
- Keys generated by a user who is access restricted later to that specific key manager remain valid and can be utilized until their expiration.