Using Kubernetes Secrets in Synapse Configurations¶
WSO2 Micro Integrator comes with a built-in secret repository as a part of its secure vault implementation by default. In addition to this, the Micro Integrator also provides built-in support for Docker secrets and Kubernetes secrets for your containerized deployments. You need to generate Kubernetes secrets for the sensitive data and inject them to the pods in your deployment as environment variables. Follow the steps given below.
Step 1: Creating the secret¶
You can generate Kubernetes secrets using the following command using kubectl.
kubectl create secret generic <secret_name> --from-literal=<key>=<value>For example, let's generate a database password:
kubectl create secret generic db-password --from-literal=password=1234567See the Kubernetes guide for more information on creating secrets.
Step 2: Adding the secret to a Pod¶
You can add the defined secret into your deployment as an environment variable of your container.
The integration artifacts you develop using WSO2 Integration Studio are built into a Docker image from the Kubernetes Exporter module. Therefore, you must update the integration_cr.yml file (in your Kubernetes Exporter module) with the secrets you generated by using the following syntax:
env:
- name: PASSWORD
valueFrom:
secretKeyRef:
name: <secret_name>
key: <key>For example, let's add the database password as an environment variable to the containers:
apiVersion: "integration.wso2.com/v1alpha1"
kind: "Integration"
metadata:
name: "kubesecrets"
spec:
replicas: 1
image: "docker/k8secret:1.0.0"
env:
- name: DB_PASSWORD
valueFrom:
secretKeyRef:
name: db-password
key: passwordStep 3: Using Kubernetes secrets in Synapse configurations¶
Secrets can be accessed from the integration artifacts by using the wso2:vault-lookup function in the following format.
wso2:vault-lookup('<alias>', '<type>', '<isEncrypted>')Specify values for the following three parameters:
<alias>: Name of the environment variable specified in theintegraton_cr.ymlfile.<type>: Set this toENV<isEncrypted>: Set this totrueorfalseto specify whether the secret is encrypted.
Given below is a sample synapse configuration with an environment variable lookup.
<property expression="wso2:vault-lookup('DB_PASSWORD', 'ENV', 'false')" name="secret"/>Step 4: Enabling secrets in the environment¶
Once the secrets are added to the environment, you need to enable secure vault in the environment. In a Kubernetes environment you don't need to manually run the Cipher tool. Follow the steps given below.
- Open your Integration Project in WSO2 Integration Studio, which contains all the integration artifacts and the Kubernetes Exporter.
-
Open the
pom.xmlof the Kubernetes Exporter module and select the Enable Cipher Tool check box as show below.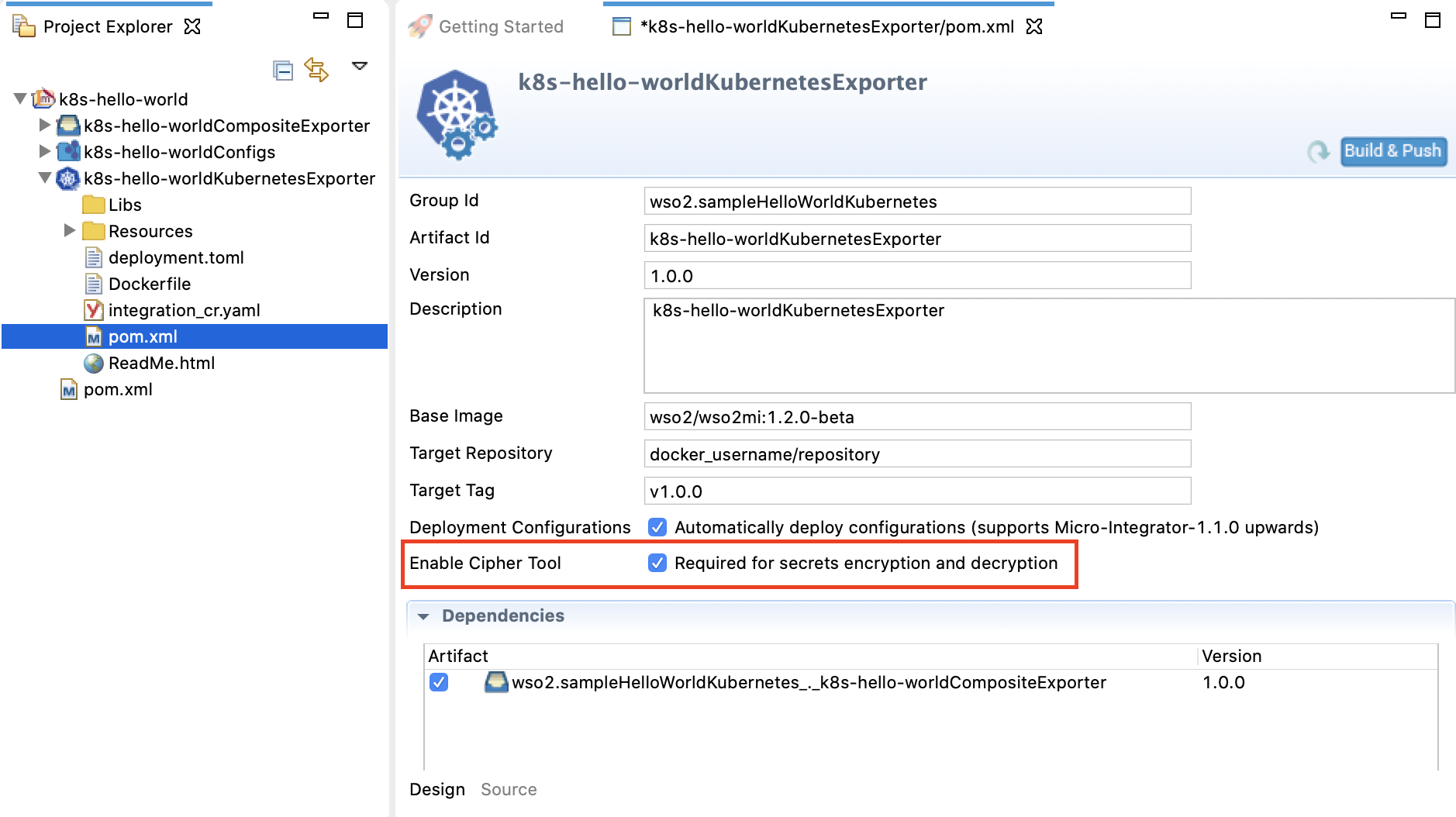
-
When you build the Docker image from your Kubernetes exporter, the secrets will get enabled in the environment.