Setting up the Amazon Lambda Environment¶
To use the AmazonLambda service, you must have an AWS account. If you do not already have an account, you are prompted to create one when you sign up. You are not charged for any AWS services that you sign up for unless you use them.
Signing Up for AWS¶
To sign up for AWS:
-
Navigate to Amazon AWS website and select Create an AWS Account.
Note: If you previously signed in to the AWS Management Console using AWS account root user credentials, select Sign in to a different account. If you previously signed in to the console using IAM credentials, choose Sign-in using root account credentials. Then select Create a new AWS account.
-
Follow the online instructions.
Part of the sign-up procedure involves receiving a phone call and entering a verification code using the phone keypad. AWS will notify you by email when your account is active and available for you to use.
Obtaining user credentials¶
You can access the Amazon Lambda service using the root user credentials but these credentials allow full access to all resources in the account as you cannot restrict permission for root user credentials. If you want to restrict certain resources and allow controlled access to AWS services then you can create IAM (Identity and Access Management) users in your AWS account for that scenario.
Steps to get an AWS Access Key for your AWS root account¶
-
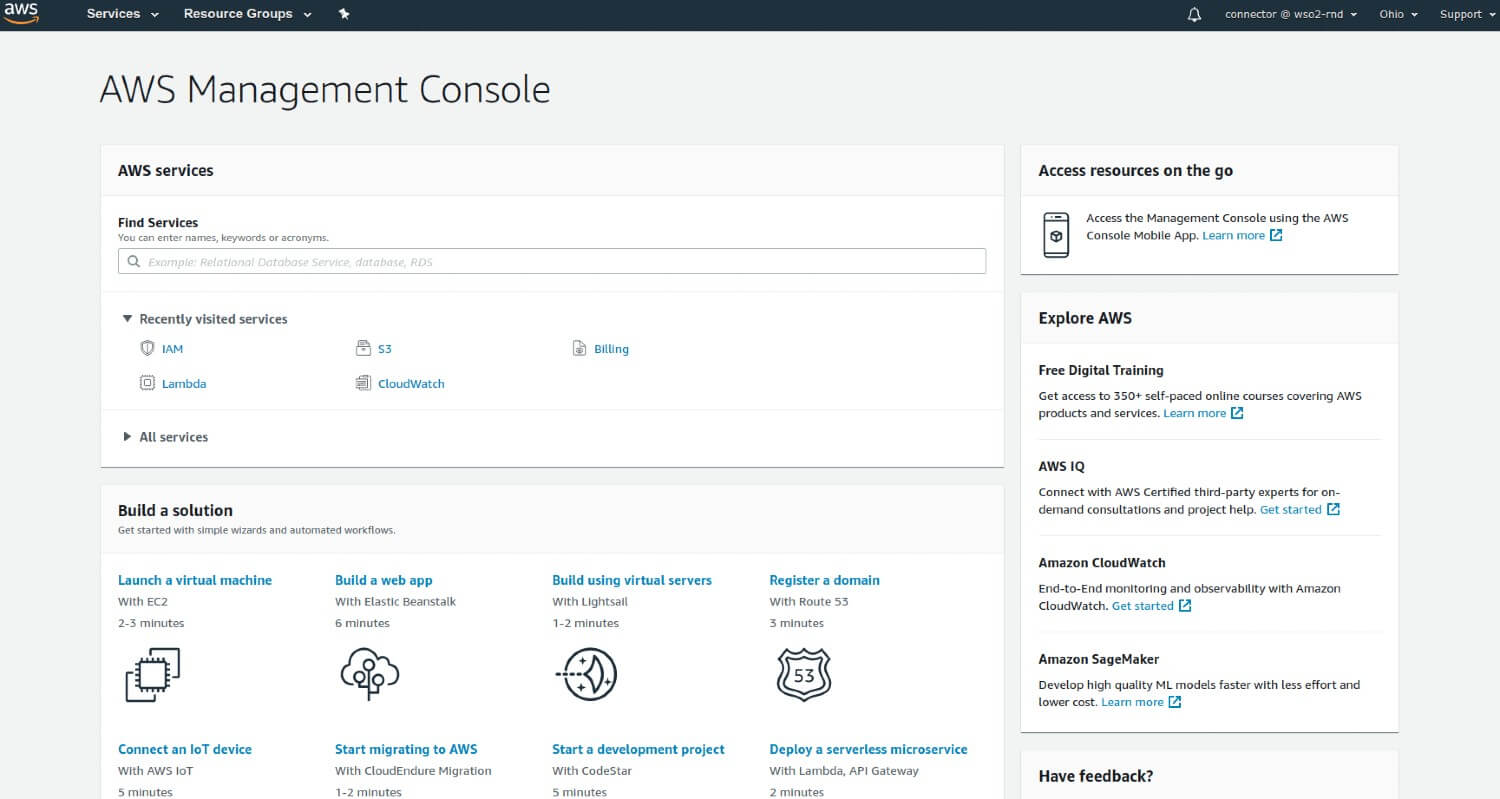
Go to the AWS Management Console.
-
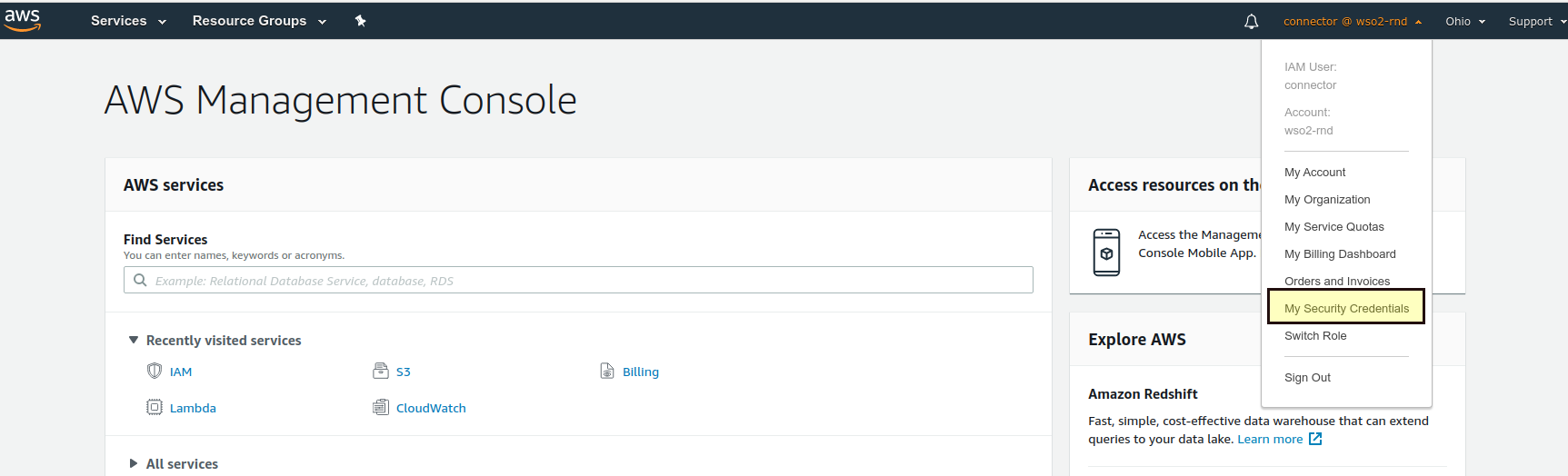
Hover over your company name in the right top menu and click "My Security Credentials".
-
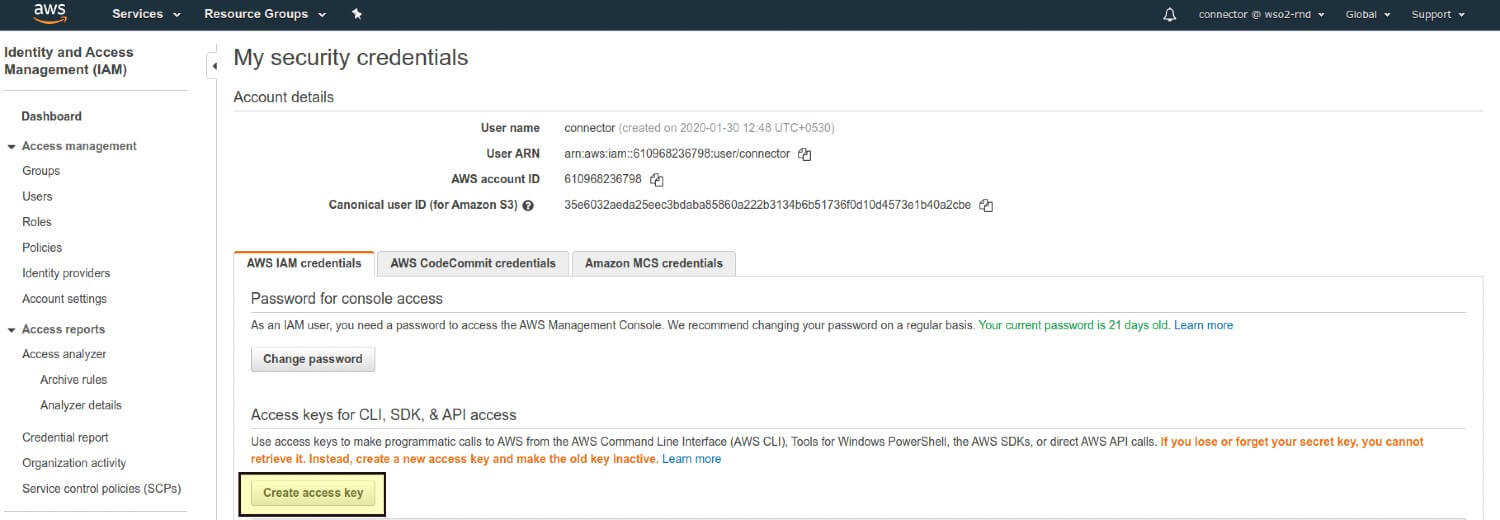
Scroll to the "Access Keys" section.
-
Click on "Create New Access Key".
- Copy both the Access Key ID (YOUR_AMAZON_LAMBDA_KEY) and Secret Access Key (YOUR_AMAZON_LAMBDA_SECRET).
Steps to get an AWS Access Key for an IAM user account¶
-
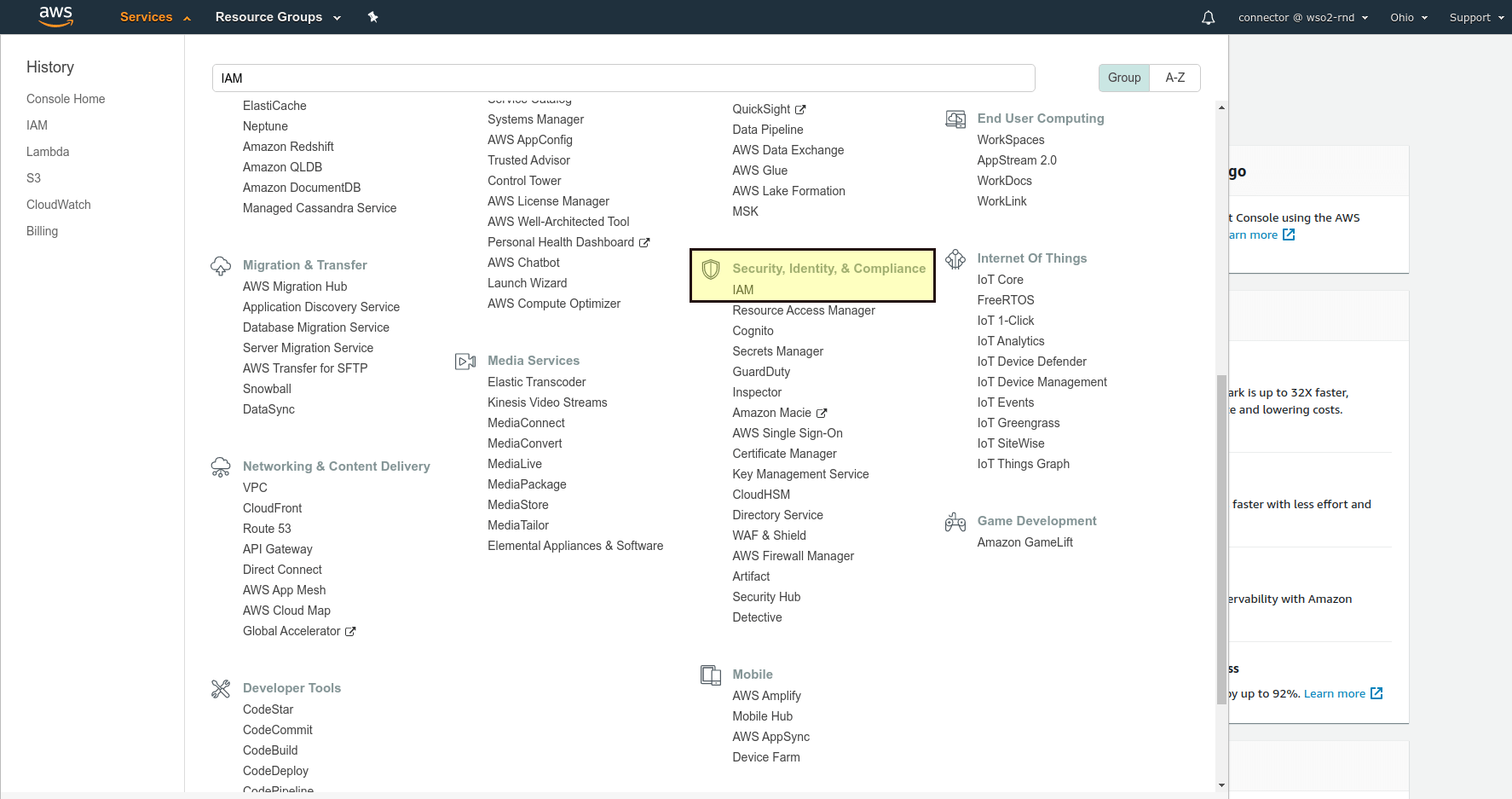
Sign in to the AWS Management Console and open the IAM console.
-
In the navigation pane, choose Users.
-
Add a checkmark next to the name of the desired user, and then choose User Actions from the top.
-
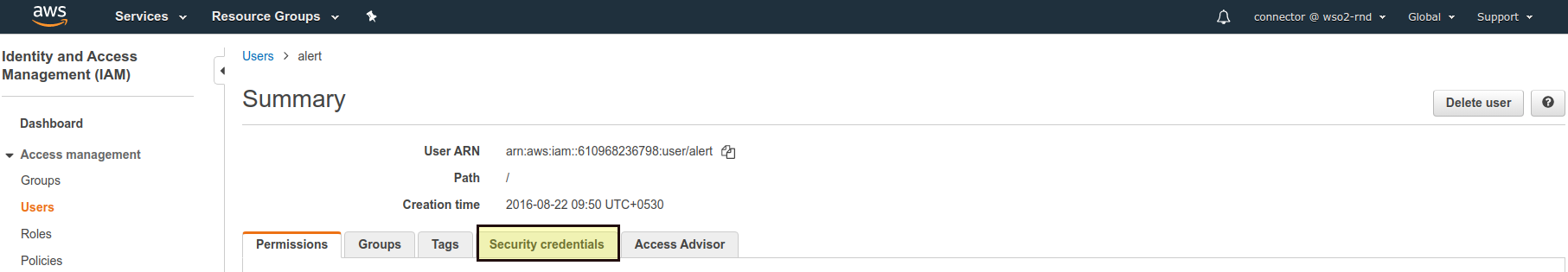
Click on Manage Access Keys.
-
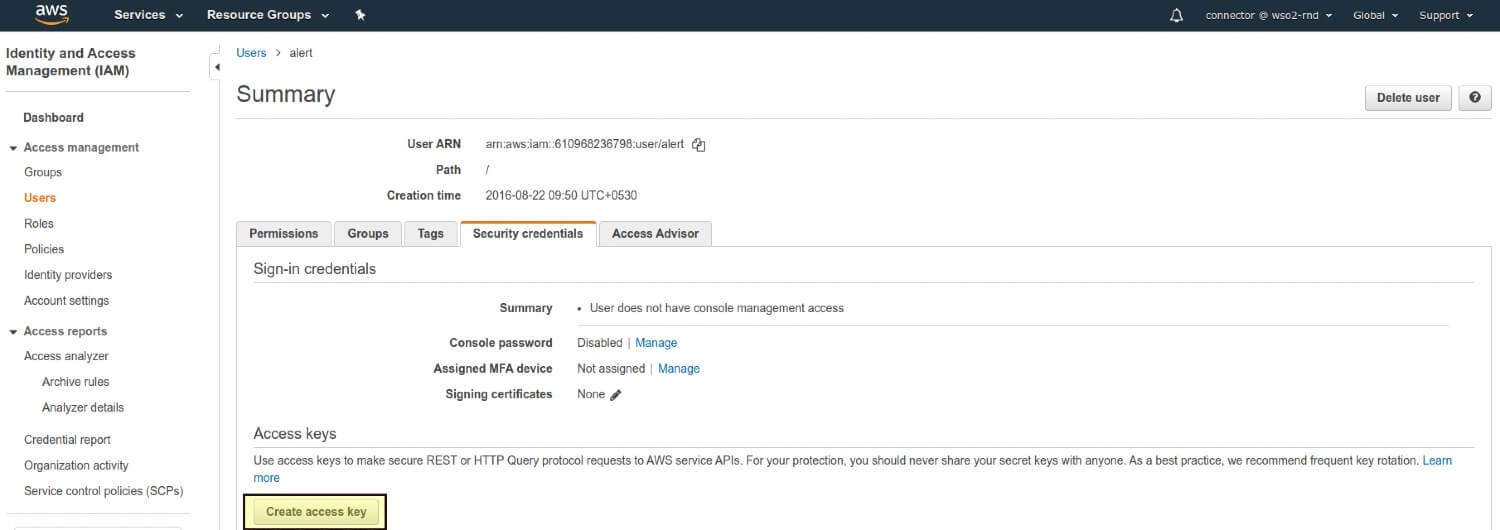
Click on Create Access Key.
-
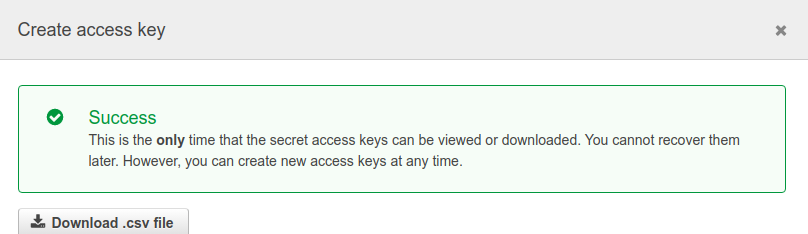
Click on Show User Security Credentials. Copy and paste the Access Key ID and Secret Access Key values, or click on Download Credentials to download the credentials in a CSV (file).
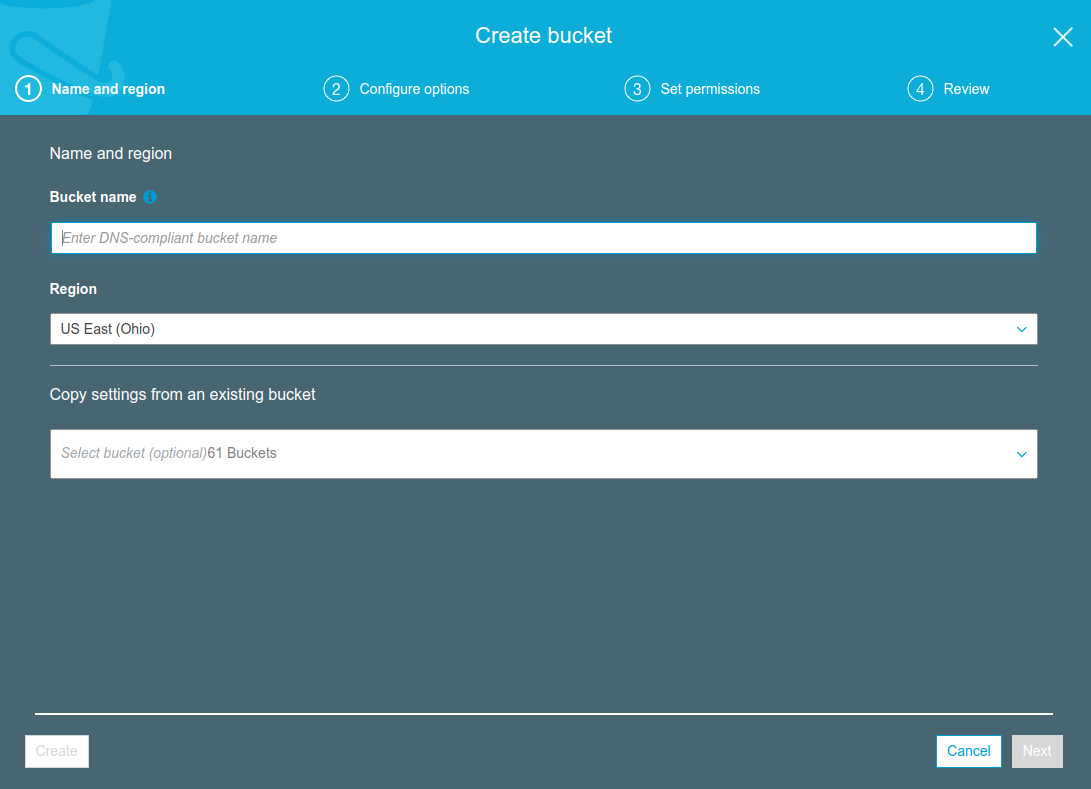
Create Amazon S3 Bucket¶
- Navigate to the created AWS account.
- Click Services tab on left top of the screen.
-
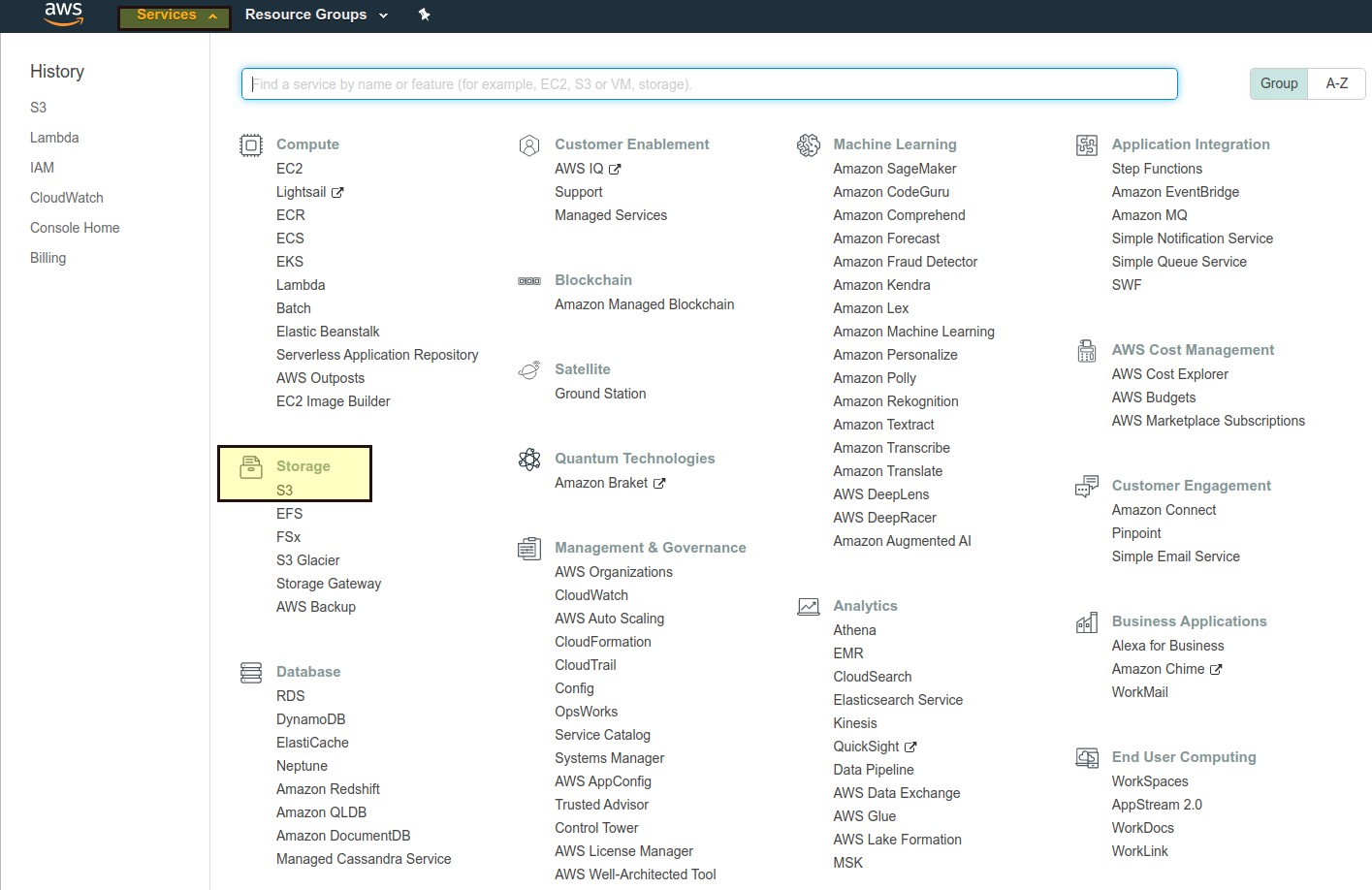
Select Storage and click S3.
-
Create a bucket.
Create Deployment Package¶
Your function's code consists of scripts or compiled programs and their dependencies. When you author functions in the Lambda console or a toolkit, the client creates a ZIP archive of your code called a deployment package.
This sample explains how to create a sample Python program as a deployment package.
- Create a sample Python function (e.g., lambda_function.py) file (on Linux and MacOS, use your preferred shell and package manager. On Windows 10, you can install the Windows Subsystem for Linux to get a Windows-integrated version of Ubuntu and Bash).
- Create a ZIP archive.
~/my-function$ zip function.zip lambda_function.py adding: lambda_function.py (deflated 17%) -
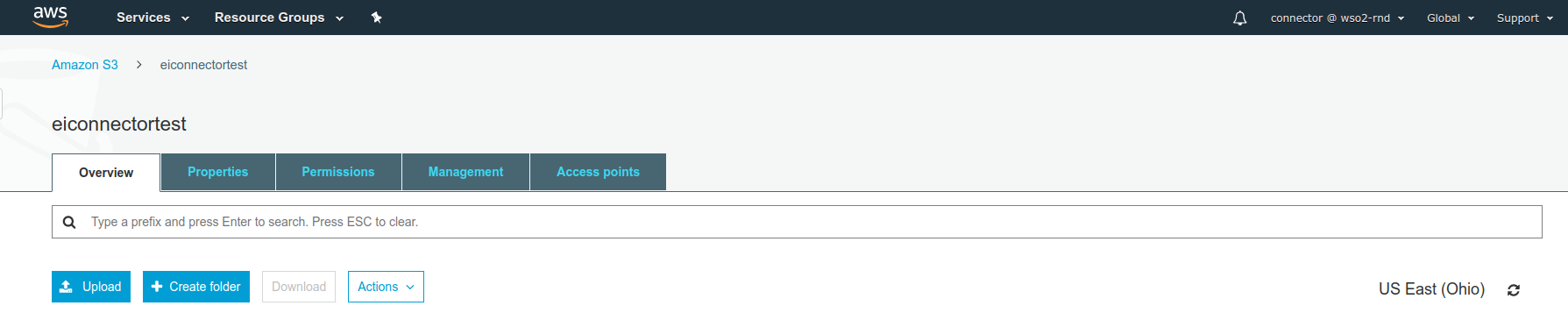
Upload the ZIP archive you created into the S3 bucket that you created.
Create Execution Role¶
You can use AWS Identity and Access Management (IAM) to manage access to the Lambda API and resources like functions and layers. For users and applications in your account that use Lambda, you manage permissions in a permissions policy that you can apply to IAM users, groups, or roles. To grant permissions to other accounts or AWS services that use your Lambda resources, you use a policy that applies to the resource itself.
Creating an Execution Role in the IAM Console.
-
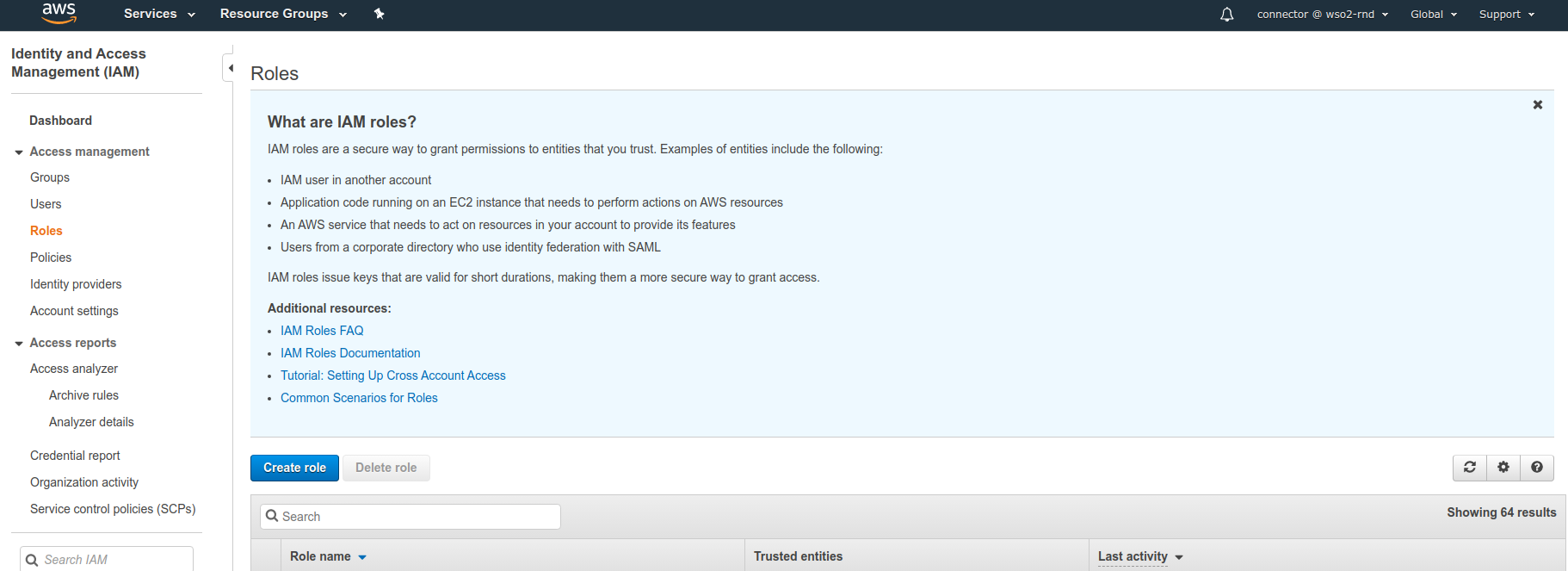
Open the roles page in the IAM console.
-
Choose Create role.
- Under Common use cases, choose Lambda.
- Choose Next: Permissions.
- Under Attach permissions policies, choose the AWSLambdaBasicExecutionRole and AWSXrayWriteOnlyAccess managed policies.
- Choose Next: Tags.
- Choose Next: Review.
- For Role name, enter lambda-role.(Please copy and save the created role and role name to configure the connector)
- Choose Create role.