Identity Management for the API Developer Portal¶
Identity management for the API developer portal includes the following features.
Apart from the above main features, there is another feature to Disable the Anonymous Access to the Developer Portal.
Password Recovery¶
Password recovery feature does not work by default because an email server is not configured to send the password recovery email. Follow the steps below to enable password recovery feature for the API Developer Portal.
-
Open the
<API-M_HOME>/repository/conf/deployment.tomlfile and add a mail server configuration as shown below. See Configuring the Email Sending Module for more information.[output_adapter.email] from_address = "[email protected]" username = "[email protected]" password = "xxxxxx" hostname = "smtp.gmail.com" port = "587" enable_start_tls = true enable_authentication = true -
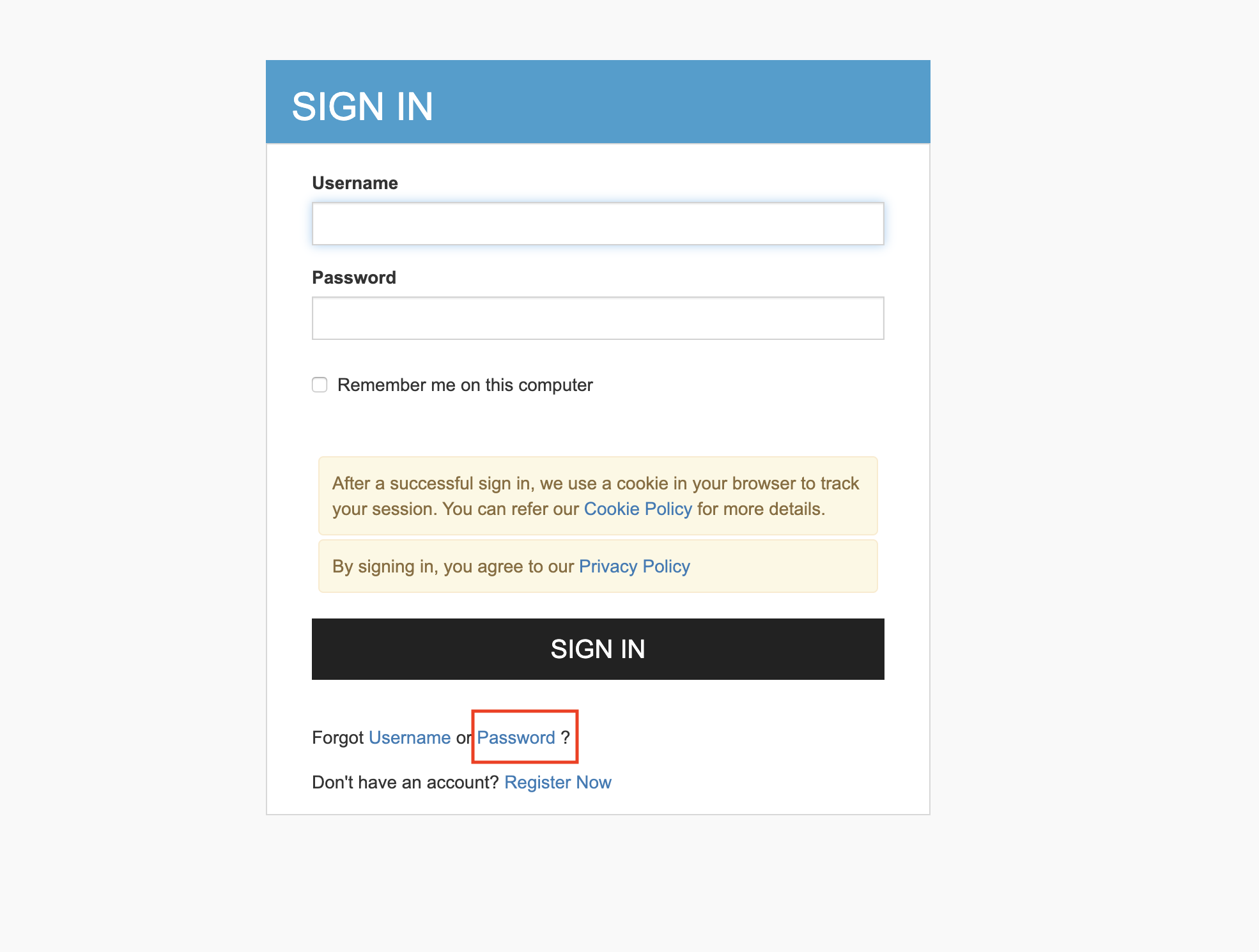
After the mail server is configured, the user can click on the Forgot Password link on the Sign In page of the API Developer Portal and request a password change.
-
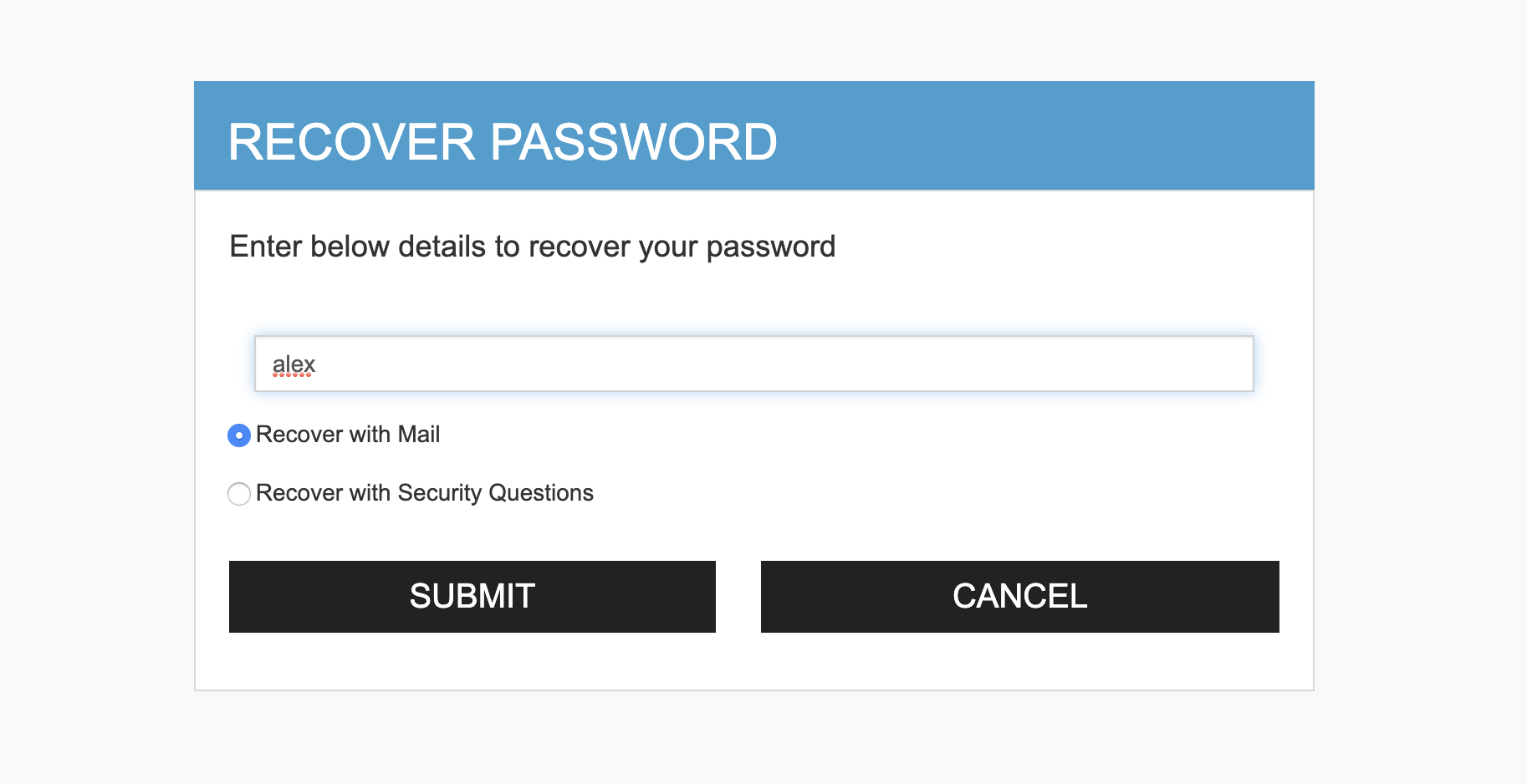
Enter the username you are trying to recover the password of and click Submit.
-
You will receive an email with instructions to reset your password. Note that this is email is sent to the email address stored during user sign up.
Note
You can change the the template of this email (E.g., email link, message body, etc.). To edit the mail template, open the
<API-M_HOME>/repository/conf/email/email-admin-config.xmlfile and make the changes.
Account locking¶
You can lock user accounts with the Account recovery and credential management feature, pre-installed in WSO2 API Manager.
Account locking by failed login attempts¶
The following steps show how to enable account locking. See Account Locking by Failed Login Attempts for more information.
-
Log into the Management Console(
https://<API-M_HOST>:<API-M_PORT>/carbon) using admin credentials.. -
Click Resident under Identity Providers found in the Main tab.
-
Expand the Login Policies tab.
-
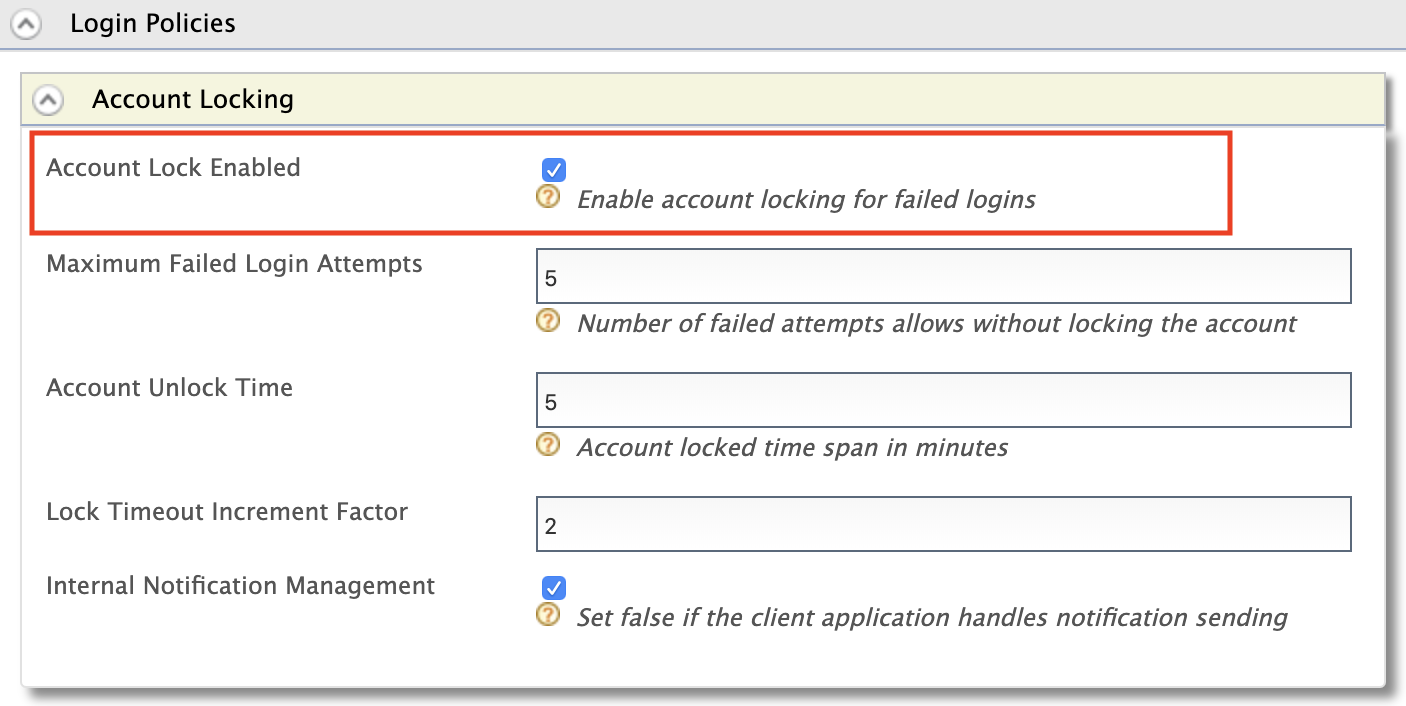
Expand the Account Locking tab and tick the Account Lock Enabled checkbox. Click Update to save changes.
Info
An error message similar to the following will be logged in wso2carbon.log when the account is locked.
ERROR - Account is locked for user alex in user store PRIMARY in tenant carbon.super. Cannot login until the account is unlocked.Account locking by an administrative user¶
An administrative user can lock and unlock a particular user's account through the management console. See Locking a Specific User Account for more information.
-
Log in to the Management Console(
https://<API-M_HOST>:<API-M_PORT>/carbon) using admin credentials. -
Go to Claims > List on the Main tab and select the
http://wso2.org/claimsclaim dialect. -
Expand the Account Locked claim and click Edit .
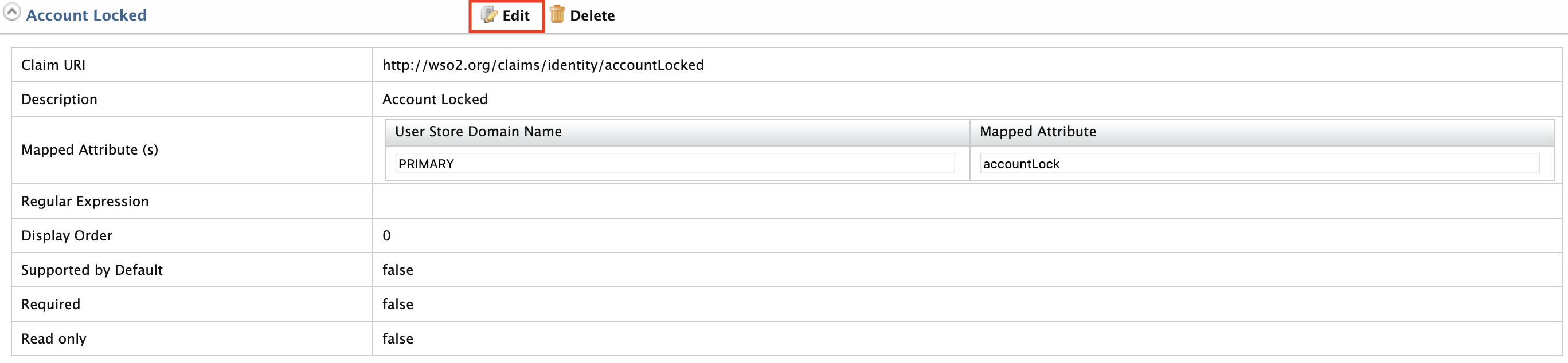
-
Tick the Supported by Default checkbox and click Update. This is done to make the Account Locked status appear in the user's profile.
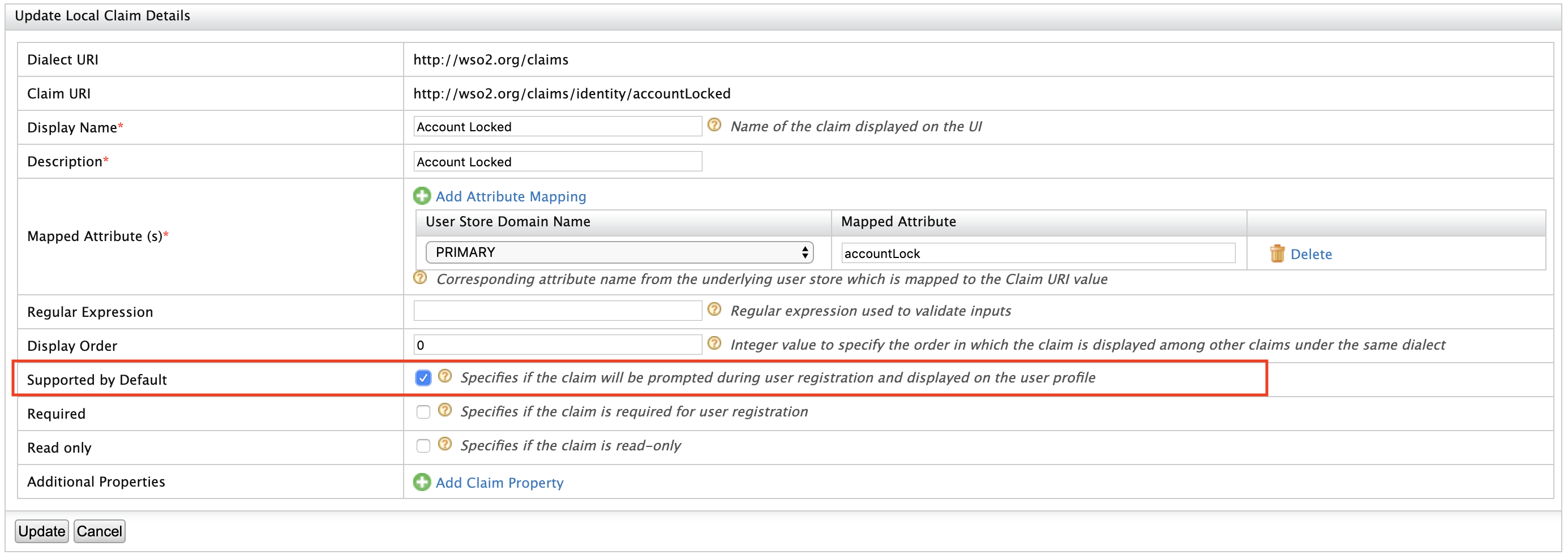
-
Go to Users and Roles > List > Users on the Main menu and click on User Profile of the user you want to lock.
-
Tick the checkbox in front of the Account Locked field to lock the account for the user and click Update .
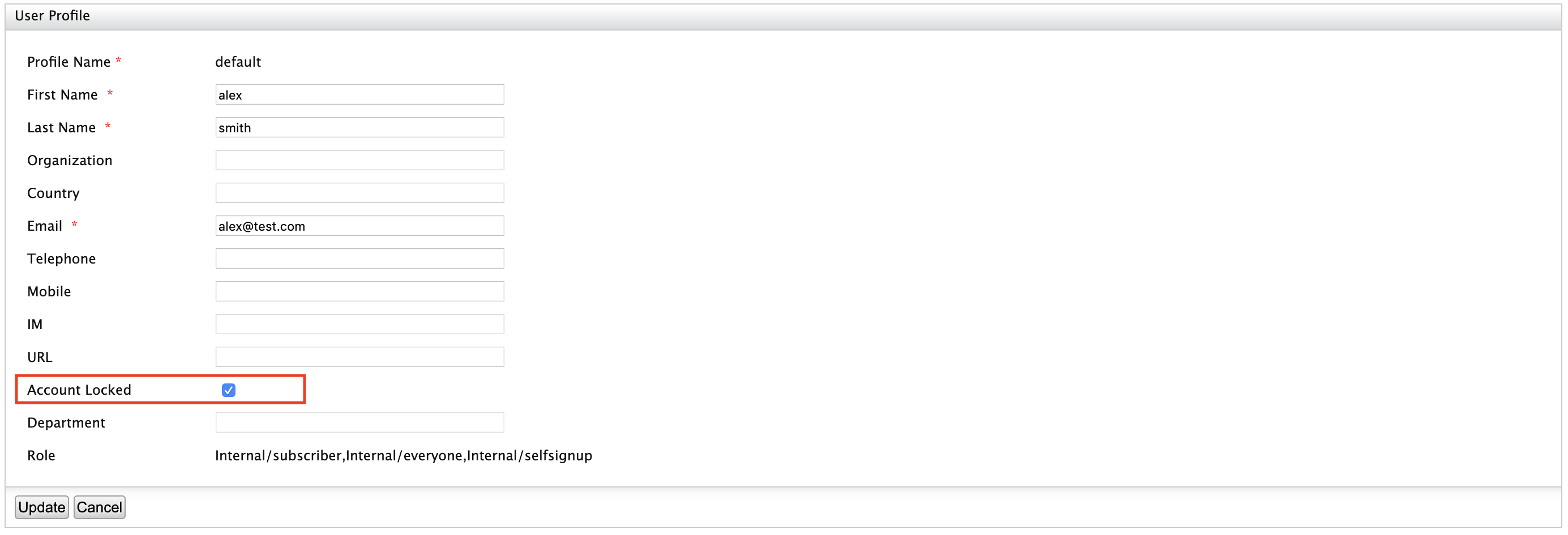
Password policies¶
You can define custom password policies for API developer portal user signup. Open the <API-M_HOME>/repository/conf/deployment.toml file and add the password policy configuration based on your preference as shown below. See Writing a Custom Password Validator for more information.
[identity_mgt.events.schemes]
passwordPolicy.properties.enable = true
passwordPolicy.properties.'min.length' = 4
passwordPolicy.properties.'max.length' = 10
passwordPolicy.properties.pattern = "^((?=.*\\\\d)(?=.*[a-z])(?=.*[A-Z])(?=.*[!@#$%&*])).{0,100}$"
passwordPolicy.properties.errorMsg = "Password pattern policy violated. Password should contain a digit[0-9], a lower case letter[a-z], an upper case letter[A-Z], one of !@#$%&* characters"
passwordPolicy.properties.'class.PasswordLengthPolicy' = "org.wso2.carbon.identity.mgt.policy.password.DefaultPasswordLengthPolicy"
passwordPolicy.properties.'class.PasswordNamePolicy' = "org.wso2.carbon.identity.mgt.policy.password.DefaultPasswordNamePolicy"
passwordPolicy.properties.'class.PasswordPatternPolicy' = "org.wso2.carbon.identity.mgt.policy.password.DefaultPasswordPatternPolicy"Disabling anonymous access to the Developer Portal¶
Warning
This feature is supported by default only from WSO2 API Manager 3.2.0 onwards. It is available for WSO2 APIM 3.0.0 only as a WUM update and is effective from 29th January 2021 (2021-01-29). For more information on how to update using WUM, see the documentation Using WSO2 Update Manager.
By default, anonymous access to the Developer Portal is enabled. Therefore, users do not need to authenticate themselves by way of signing in when accessing the Developer Portal in WSO2 API Manager. However, if required, you can disable anonymous access to the Developer Portal to prevent anonymous users from accessing the Developer Portal. When anonymous access is disabled, users will not be allowed to access the Developer Portal UI without appropriate login details or an access token.
Follow the instructions below to disable anonymous access to the Developer Portal for a particular tenant:
-
Sign in to the WSO2 API-M Management Console as a tenant admin user.
https://<API-M_host>:<API-M_port>/carbon -
Navigate to Main > Resources > Browse
-
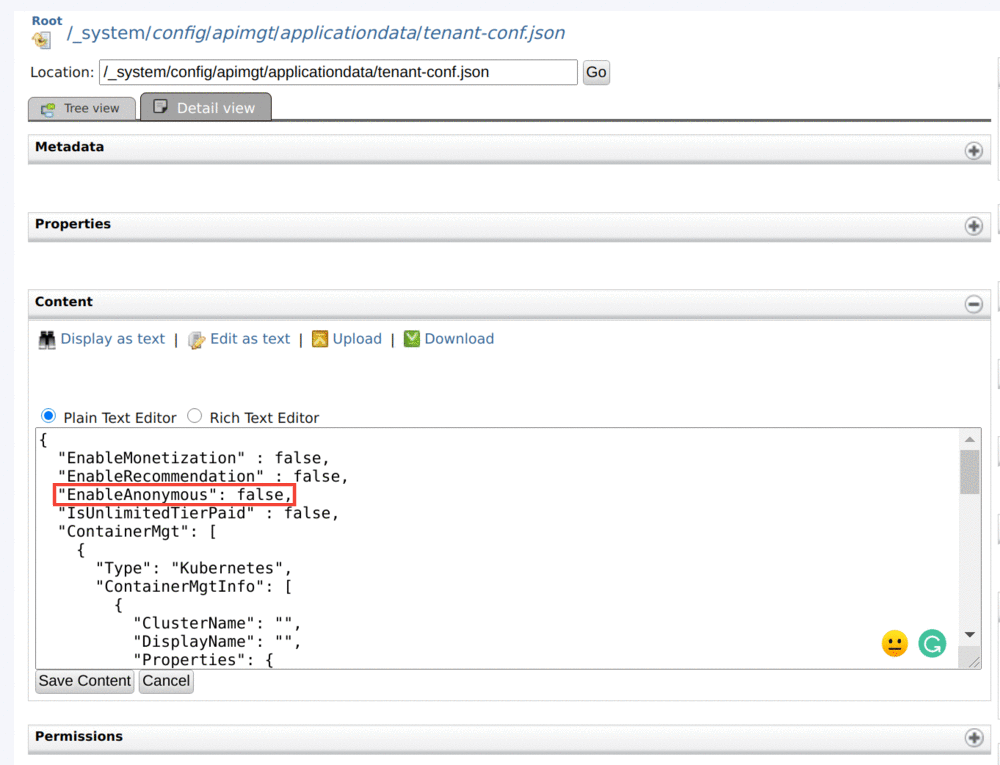
Enter
/_system/config/apimgt/applicationdata/tenant-conf.jsonas the location and click Go to browse the registry and locate the required resource. -
Add the field named
EnableAnonymouswith the valuefalseto thetenant-conf.jsonas shown below.Note
To disable anonymous access globally, add the following to the
<API-M_HOME>/repository/conf/deployment.tomlfile. ```toml [apim.devportal] enable_anonymous_mode=false -
Restart the server or wait for 15 mins until the registry cache expires.
-
Navigate to the Developer Portal.
https://<API-M_host>:<API-M_port>/devportalYou will be automatically redirected to the Sign In page if you have not previously authenticated yourself by signing in to the Developer Portal.
Info
If you have a multi-tenant environment, when you navigate to
https://<API-M_host>:<API-M_port>/devportal, it will ask you to select the tenant first. When you select a tenant, if the anonymous mode is disabled for that tenant (by following the above steps), you will be redirected to the Sign In page if you have not previously authenticated yourself by signing in to the Developer Portal.