Using OKTA As An External IDP With SAML
In the following document we will explain how to connect OKTA as a third party Identity provier to WSO2 API-Manager. Before we start first make sure you have all the pre-requisites mentioned below.
Pre-requisites¶
- Create an account in https://developer.okta.com/
- Download WSO2 API Manager 3.1.0 distribution from
- Unzip the distribution and open the
deployment.tomlfile located in<APIM_HOME>/repository/conf/and add the following configuration
This is needed since OKTA uses the email as the username by default, therefore to use the email as the username in WSO2 API-Manager we have to enable it since it not enabled by default.[tenant_mgt] enable_email_domain= true - Start the Server.
Setup OKTA¶
-
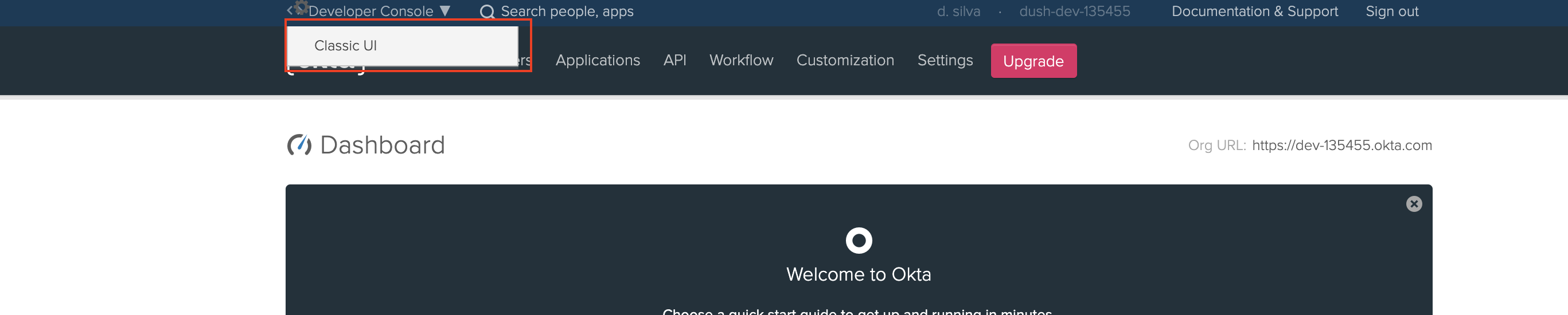
Login to the okta developer console and switch to the classic UI.
-
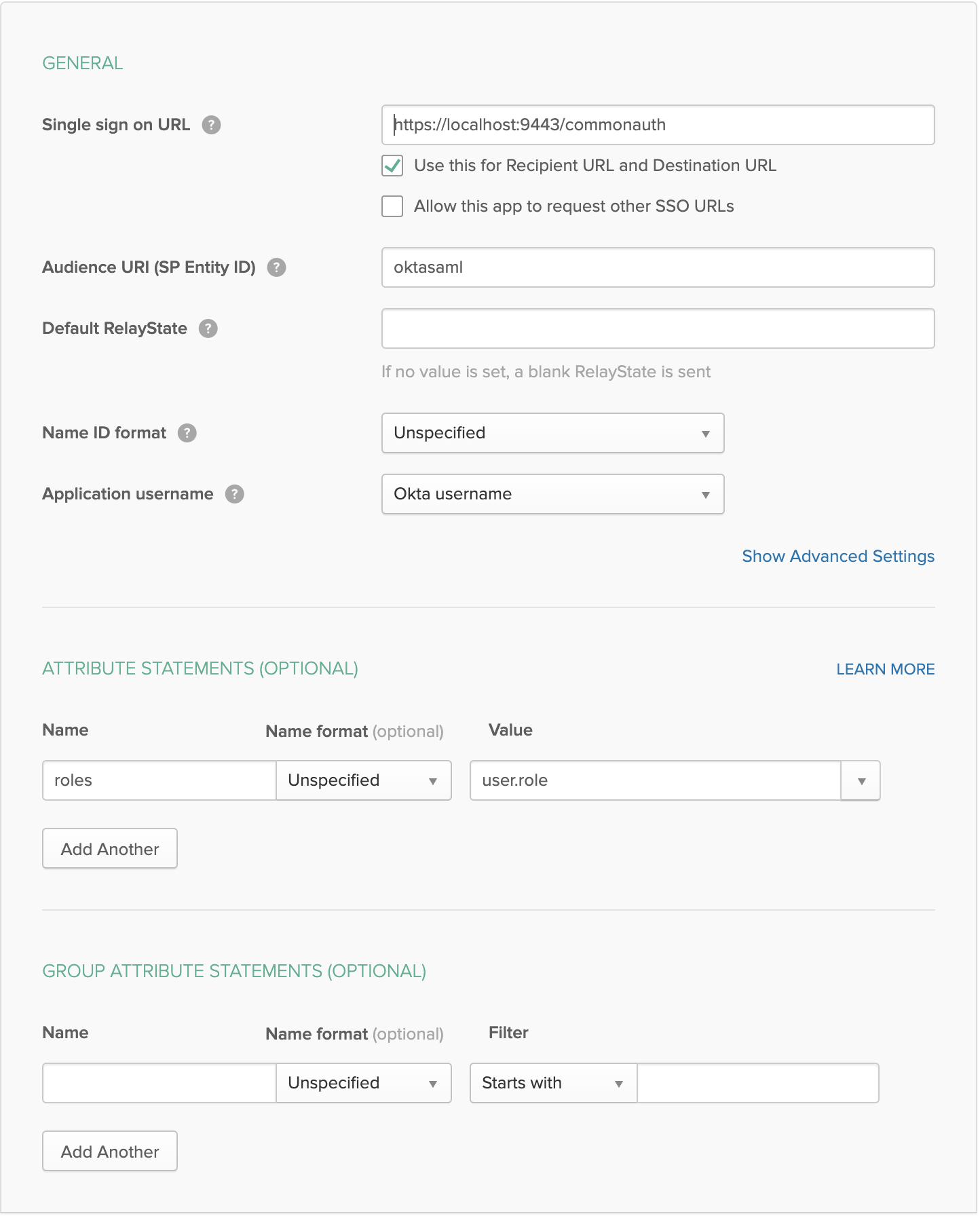
Go to Applications -> add application -> create new application and follow the details below

Select web type and saml 2.0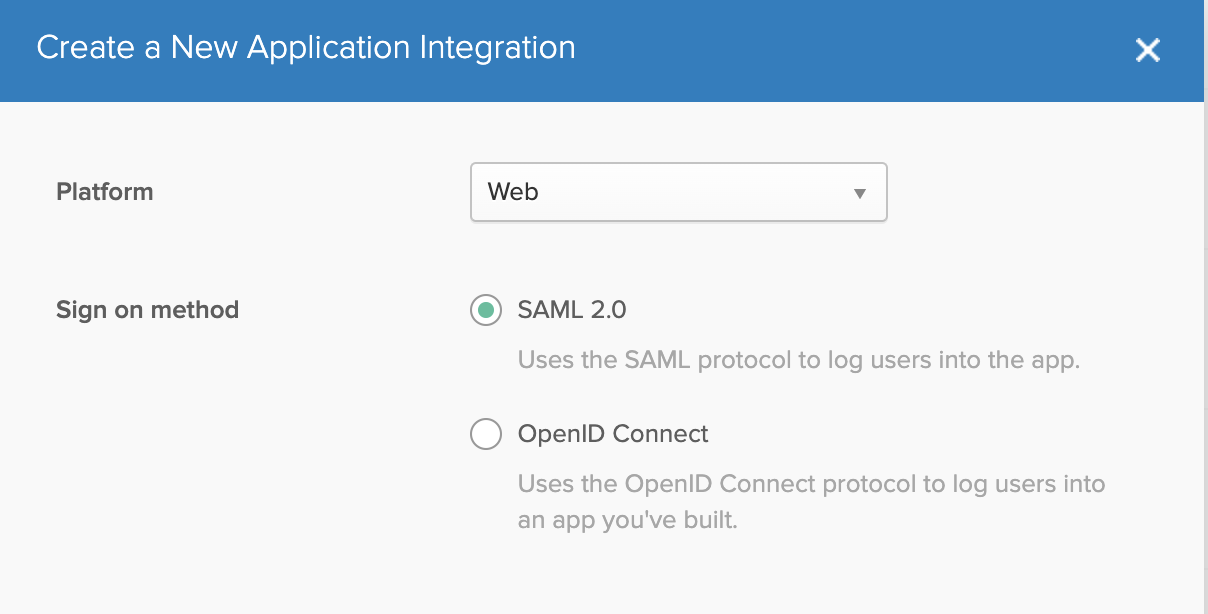
Warning
Audience URI should be same as the identity provider entity id name that is created in WSO2 API-Manager
-
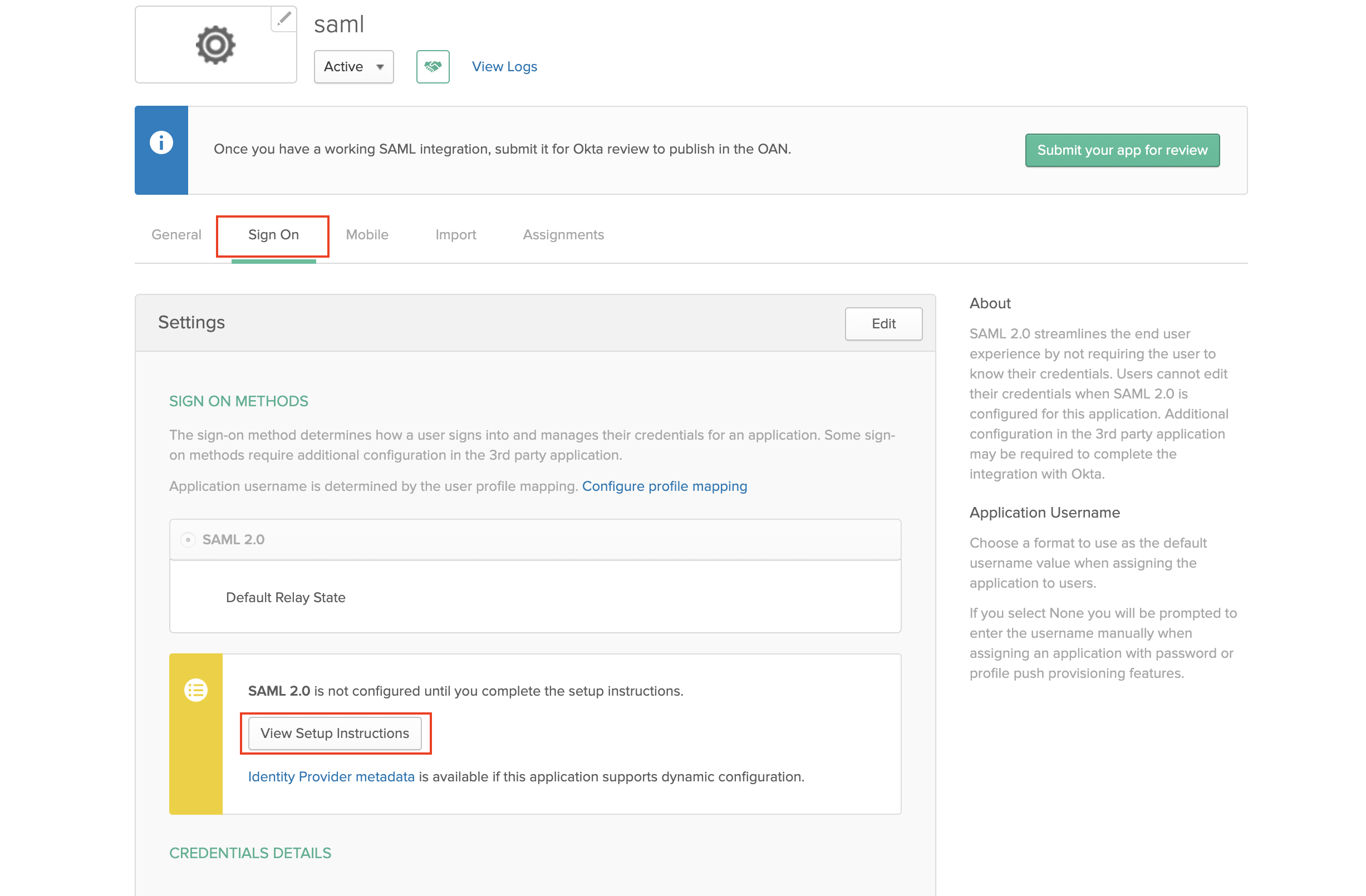
Inside the saml app you created go to sign on -> view setup instructions which will redirect you to a another page which contains okta saml related configurations.
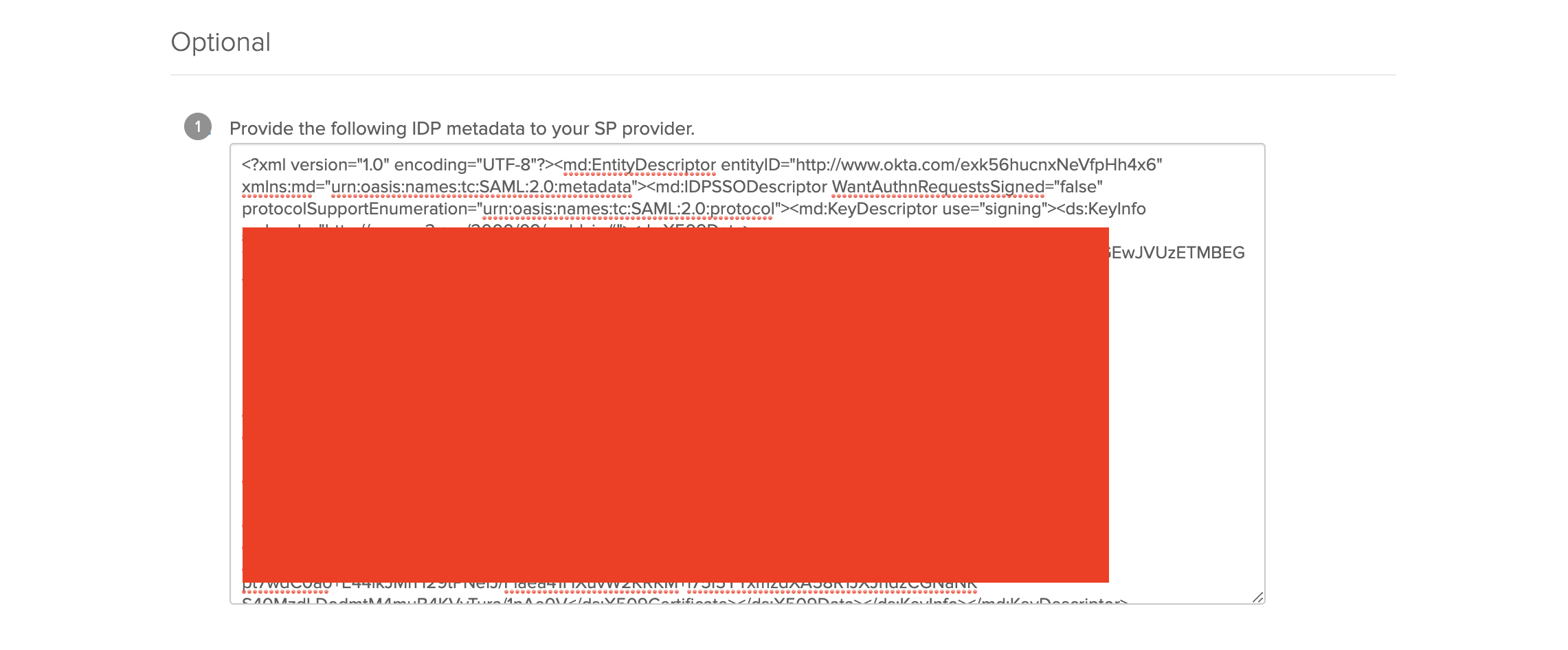
Scroll to the bottom of the page which has Provide the following IDP metadata to your SP provider.. Copy and save the details given to a xml file.
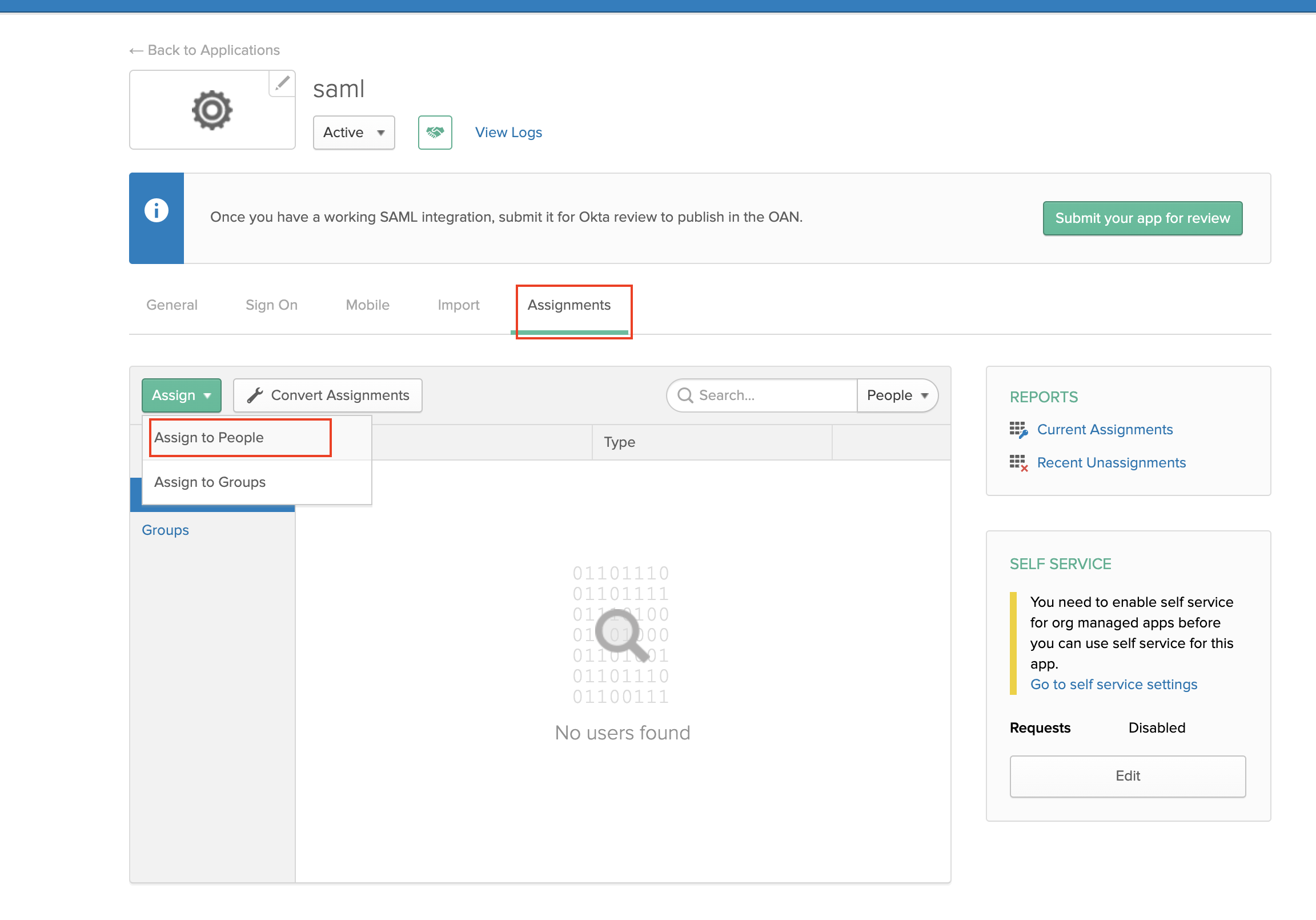
Go to assignments -> assign -> assign to people and assign your current user
-
Switch back to the developer console same as step 1
-
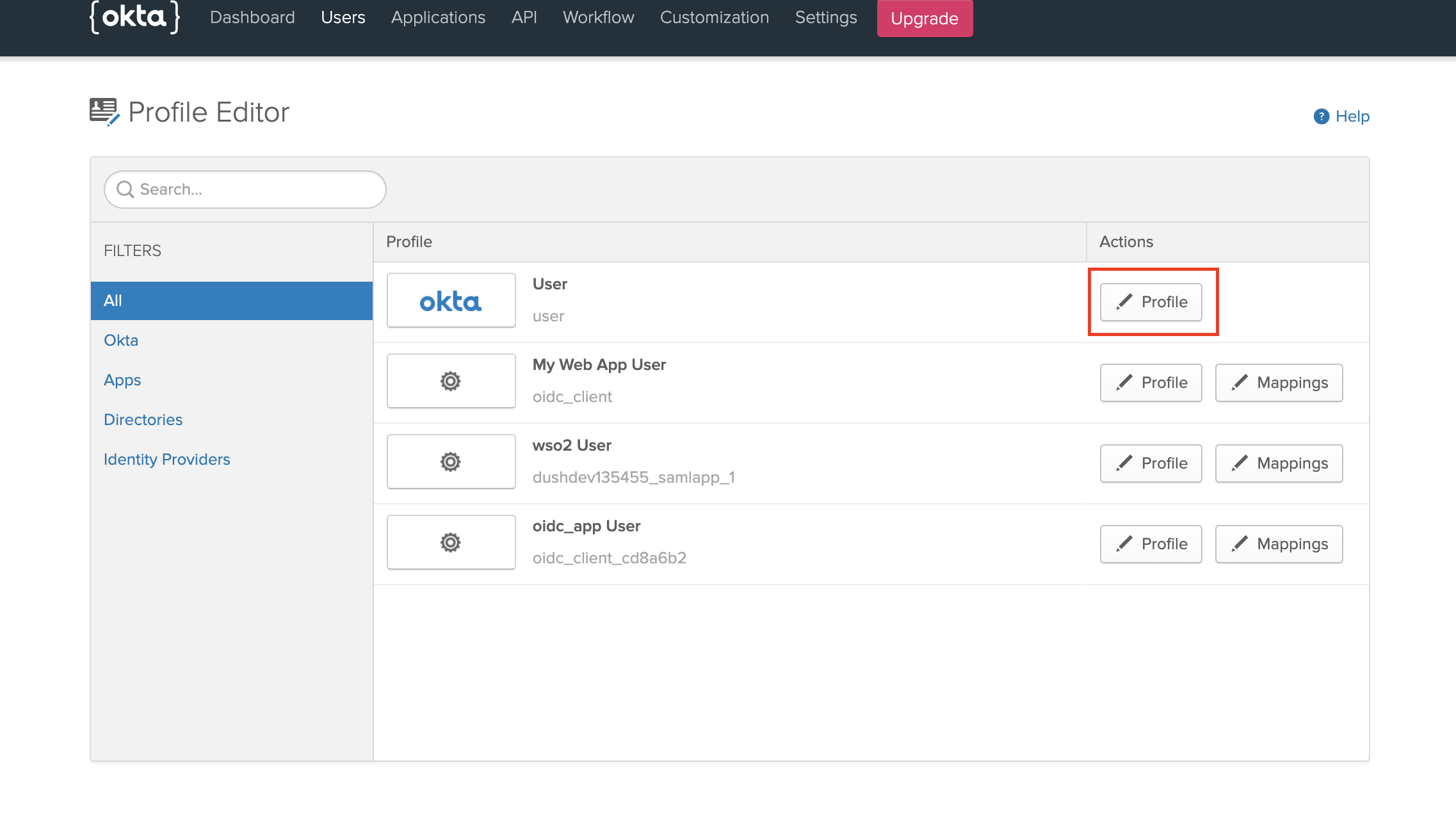
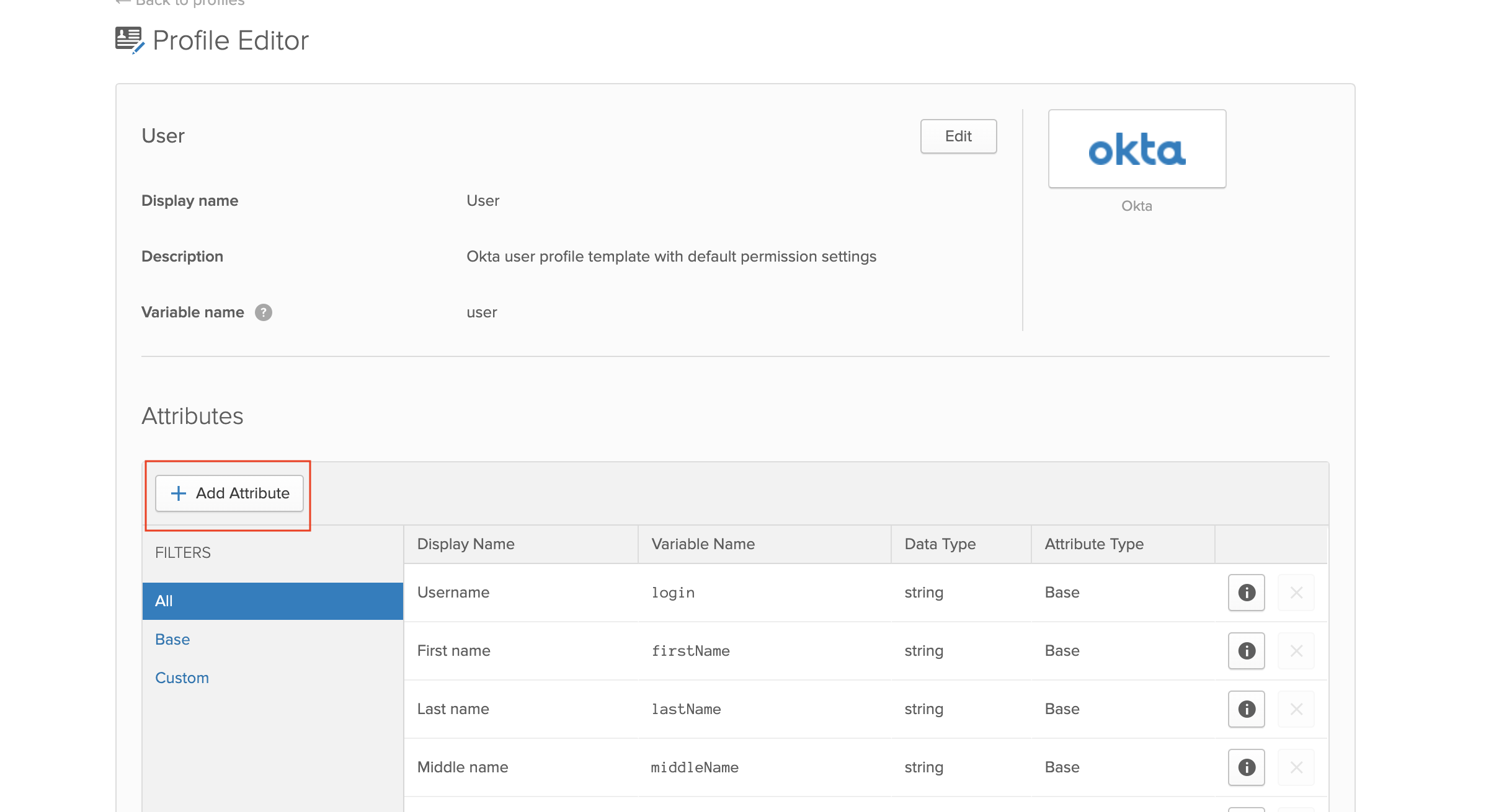
Next we need to add a new attribute to the default user profile of OKTA to epresent the user role. Navigate to Users -> Profile Editor and click on the pencil icon to edit the default profile
-
Enter the following details and click save
-
Go to Users -> People and click on your profile name. And navigate to the profile edit page as shown below


add the following role value. This will be used in the API-Manager to map an internal role to user that will be provisioned.

Setup API-Manager¶
-
Login in to
https://localhost:9443/carbon. -
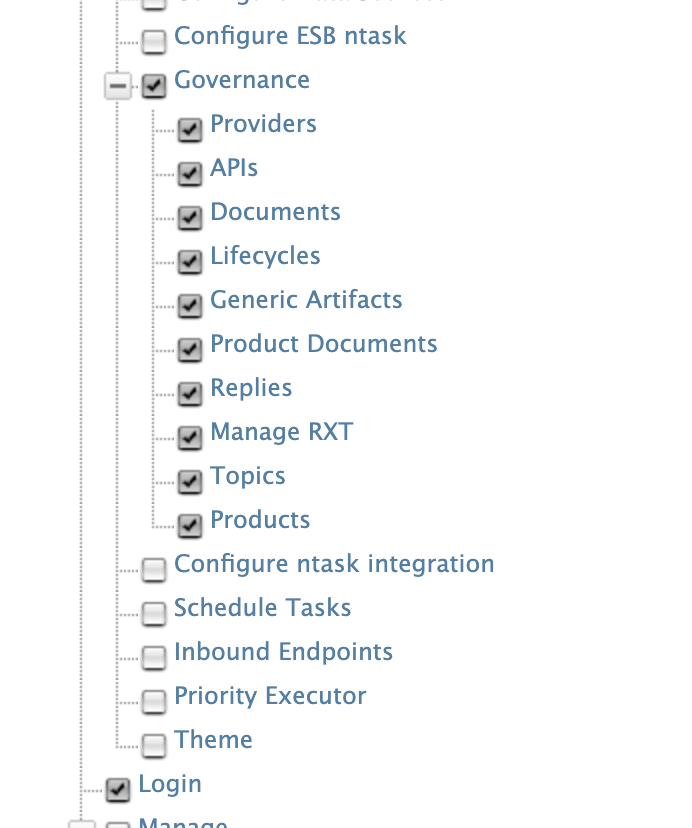
First we need to create a role that needs to be assinged to users that will be provisioned from okta. click on add in Users and Roles section and add a new role.


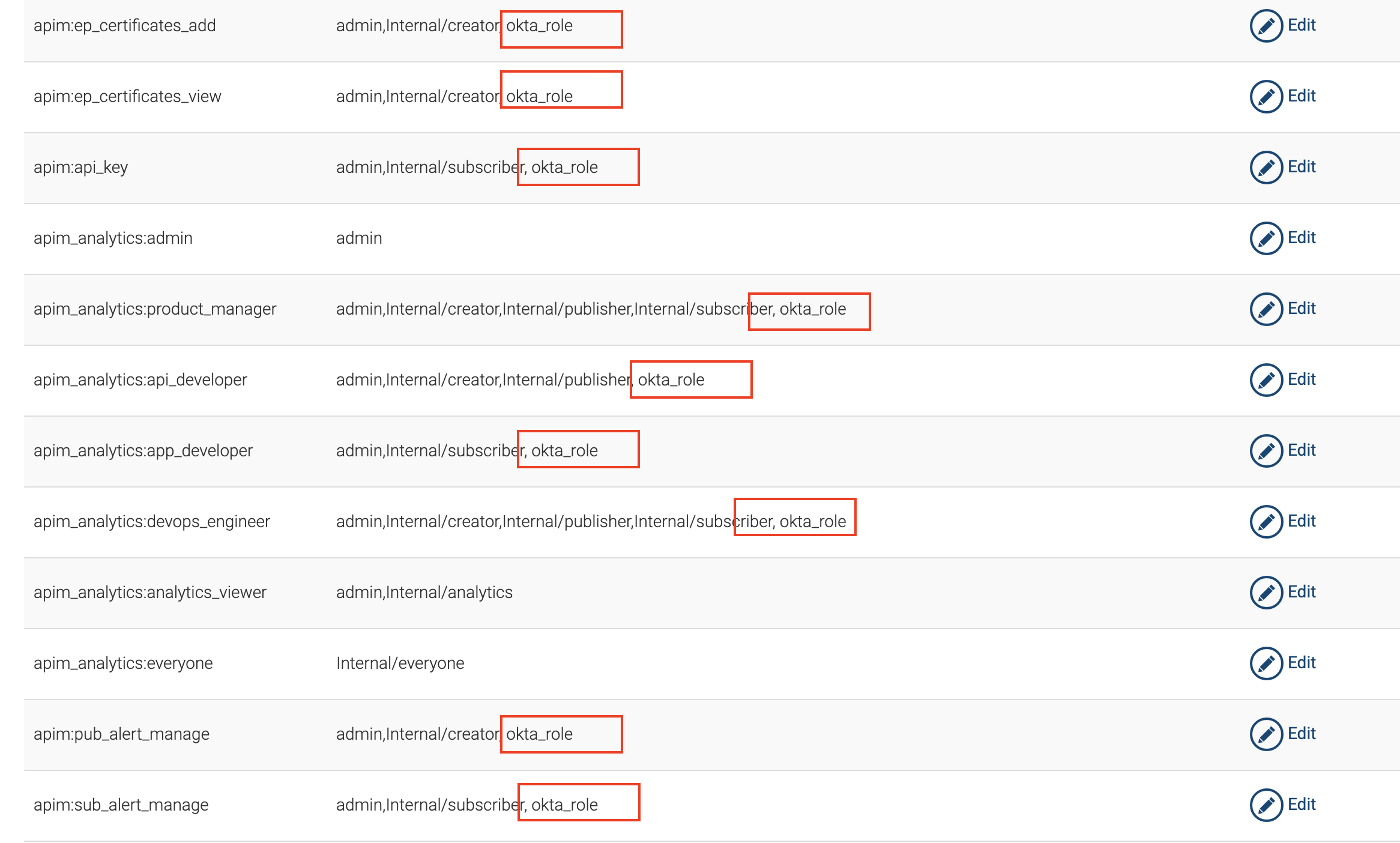
Assign the following permissions to the role and save


-
Login to
https://localhost:9443/adminexpand settings & click on scope mapping
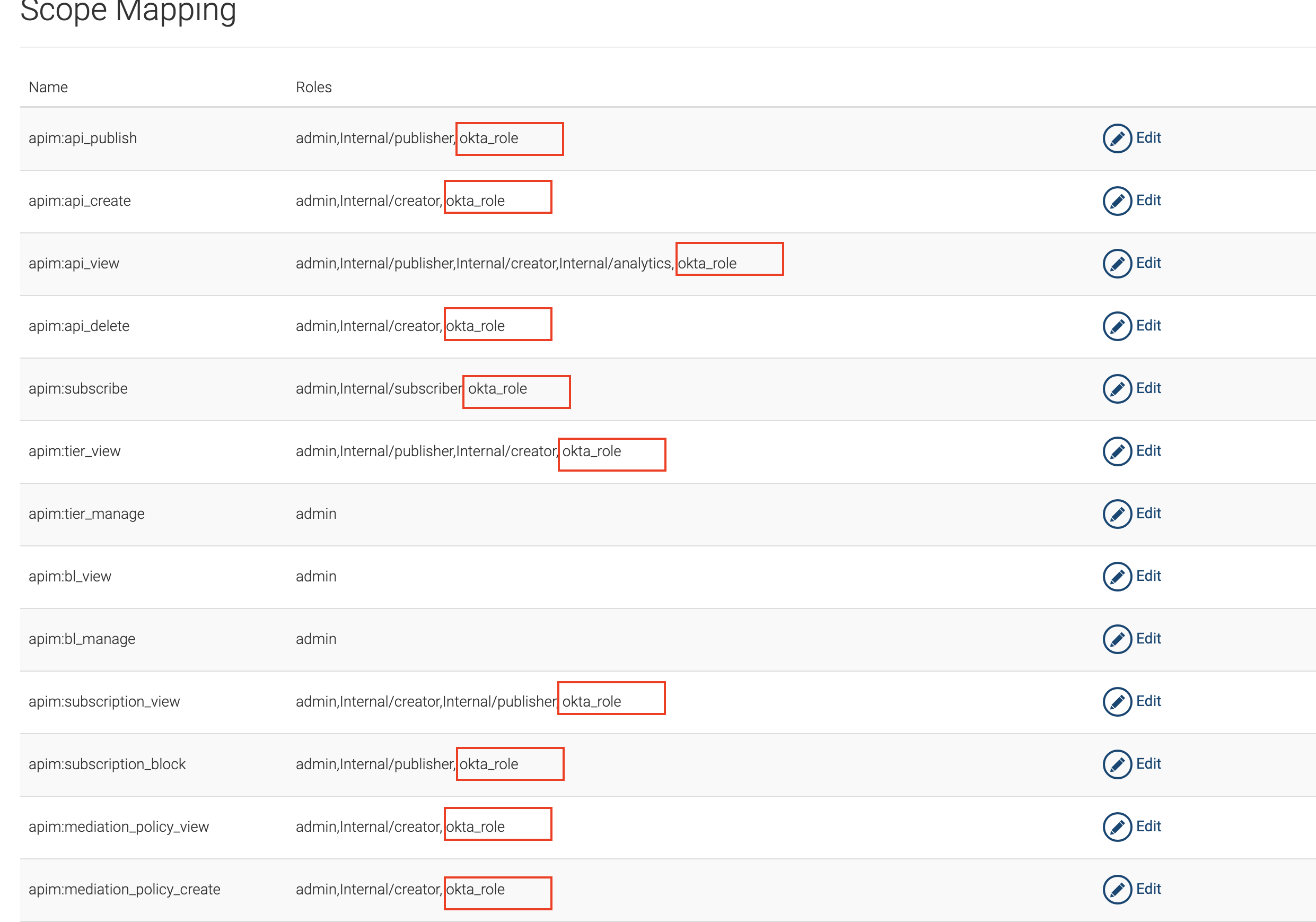
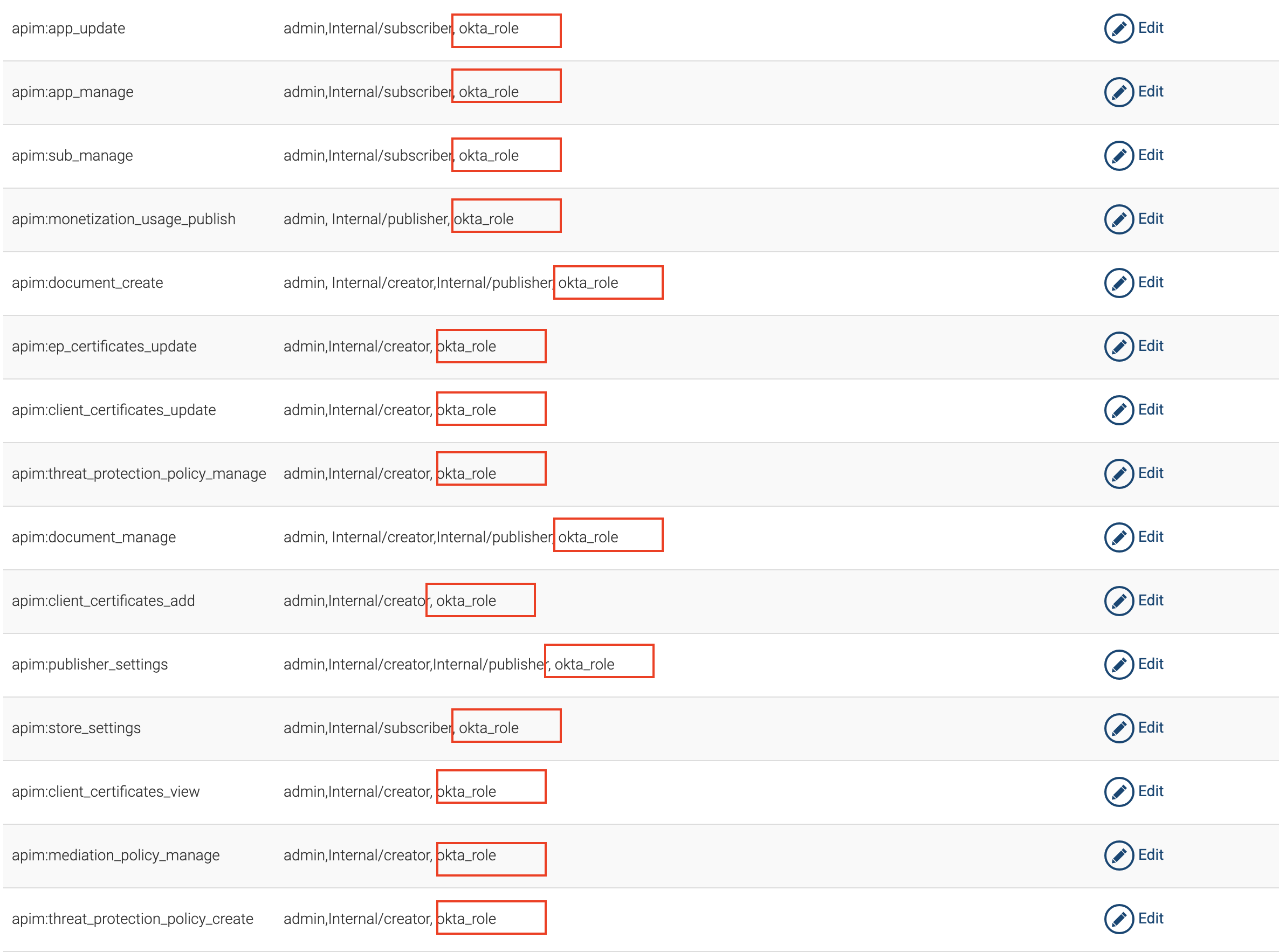
Update the following scopes with the okta_role
This will allow the user a user having the okta_role to login to Publisher and Developer Portal
-
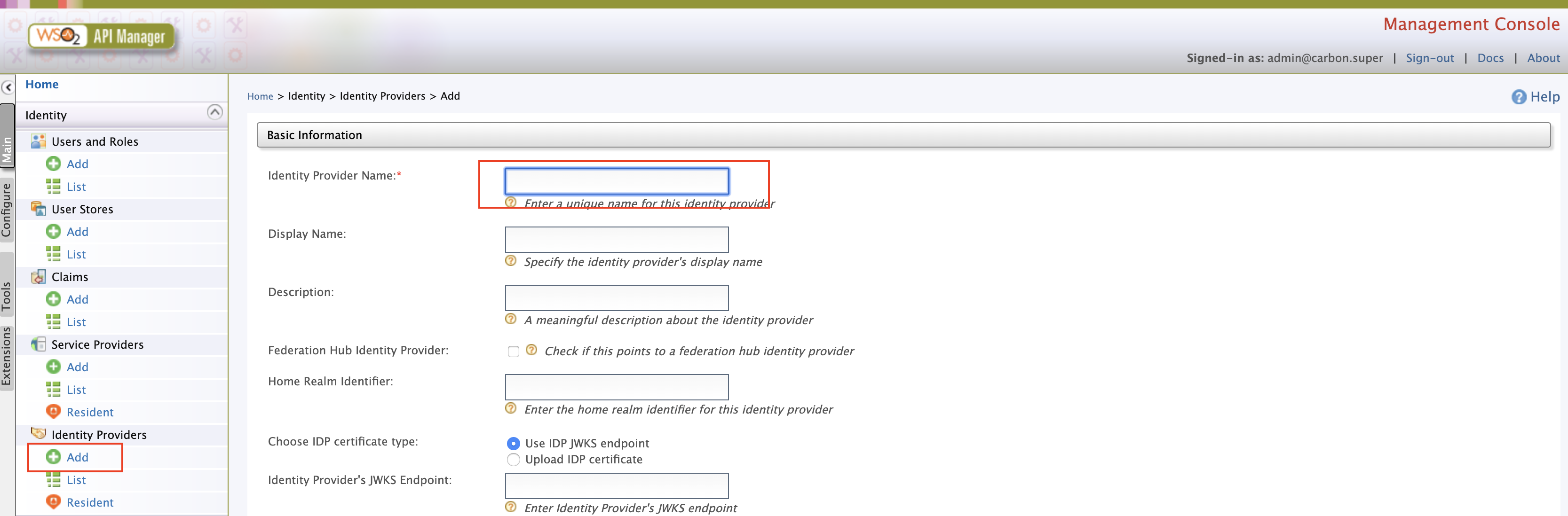
Login in to
https://localhost:9443/carbon& Click on add in identity providers section. Enter Identity Provider Name.Expand the federated authenticators -> SAML2 Web SSO Configuration section and under Select Mode select Metadata File Configuration and update the xml file that was saved during the okta setup process.
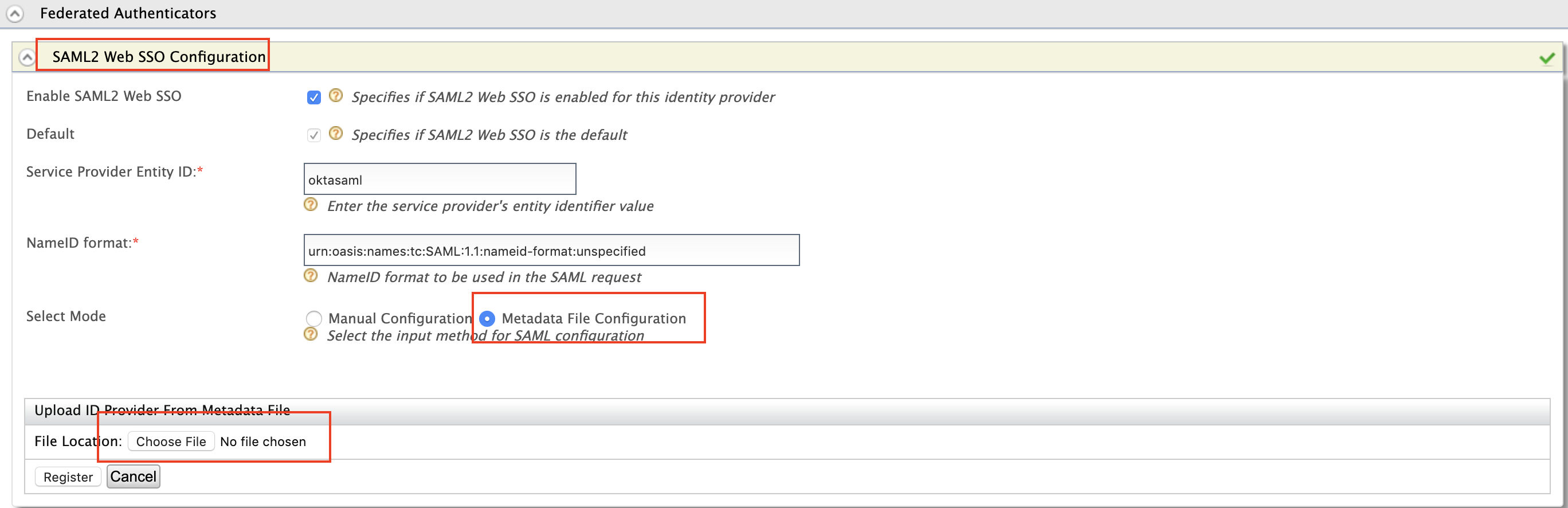
Field Sample value specifies if SAML2 Web SSO is enabled for this identity provider True Service Provider Entity ID Entity id specified when creating saml app (eg: oktasaml) -
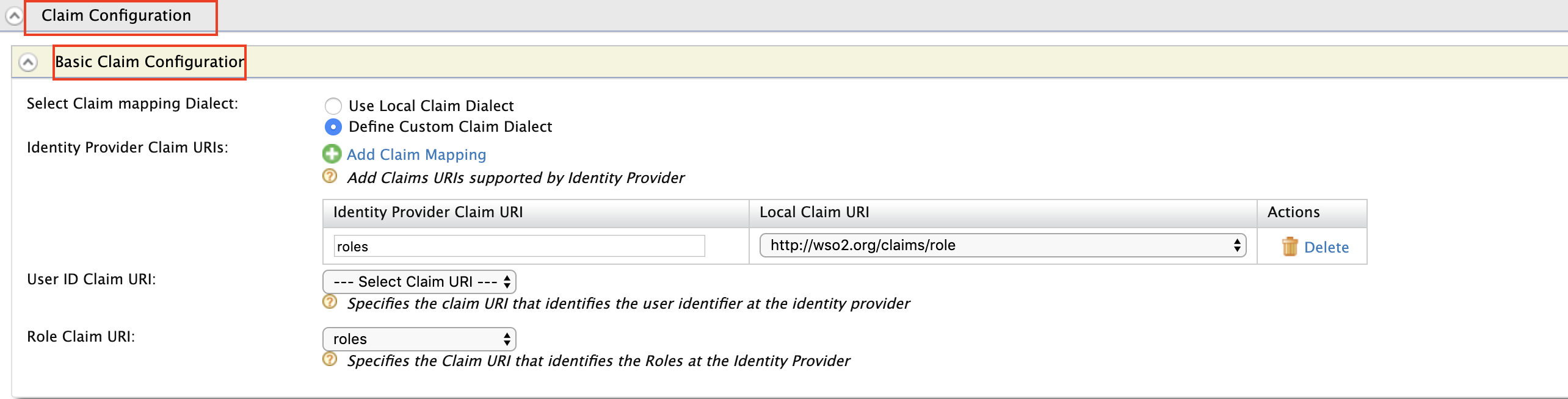
Expand Claim configuration -> Basic claim configuration and add the following claim configurations
-
Expand Role configuration and add the following role. Here we check if the user that is being logged in has the role
anyand assign him the local role okta_role
-
Enable Just in time provisioning so that the user will be saved in the API-Manager user store

-
Navigate to Service providers -> list as shown below. There are two service providers created apim_publisher, apim_devportal. Click on edit on apim_publisher.
Warning
You will have to logged into the Developer Portal and Publisher at least once for the two service providers to appear as it is created during first login.
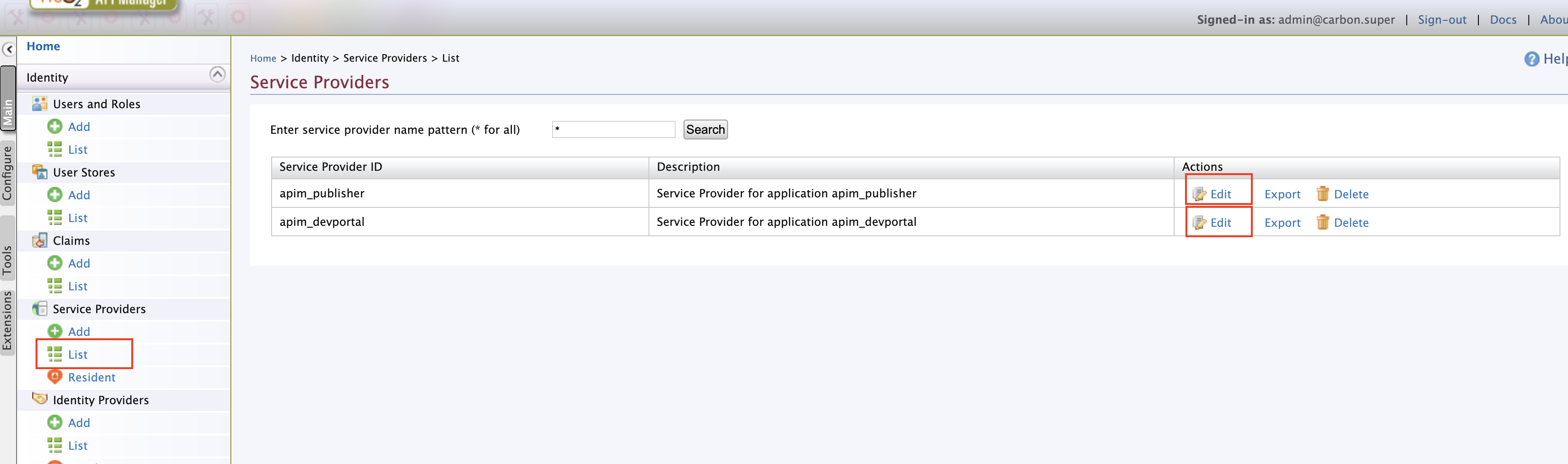
Expand local and outbound authentication configuration and under federated authentication select the name of the identity provider you created.

Repeat the same for apim_devportal service provider.
Now you are able to login to the Publisher & Developer Portal using OKTA.
Top