Configuring Identity Server as External IDP using SAML¶
The Single Sign-On with SAML 2.0 feature in the API Manager is implemented according to the SAML 2.0 browser-based SSO support that is facilitated by WSO2 Identity Server. This feature is available in any WSO2 IS version from 4.1.0 onwards. WSO2 IS 5.10.0 is used in this guide. WSO2 Identity Server acts as an identity Service Provider of systems enabled with single sign-on, while the Web applications act as SSO Service Providers. Using this feature, you can configure SSO with SAML 2.0 across the API Publisher and Developer Portal. After configuring, you can access the Developer Portal or API Publisher in a single authentication attempt.
Prerequisites¶
-
Download the API Manager 3.1.0 distribution.
- Access the previous WSO2 API Manager related releases.
- Select version 3.1.0.
- Download the API Manager.
-
Download the Identity Server 5.10.0 distribution from https://wso2.com/identity-and-access-management/.
Info
To use WSO2 IS as the Key Manager, download the WSO2 Identity Server 5.10.0 as a Key Manager pack, with pre-packaged Key Manager features as follows:
- Access the previous WSO2 API Manager related releases.
- Select version 3.1.0.
- Click on the Identity Server as a Key Manager download option.
Tip
For testing purposes if you want to run both the WSO2 API Manager and WSO2 Identity Server on the same server, then you can go to the
<IS_HOME>/repository/conf/deployment.tomlfile and offset the port by 1 by adding the following configuration:[server] offset=1 -
Start the servers using the following commands:
wso2server.bat --runsh wso2server.sh
Step 1 - Configure WSO2 Identity Server¶
Step 1.1 - Configure the Service Provider¶
-
Sign in to the Management Console of IS server.
https://{is-ip}:9444/carbon -
Navigate to the Service Providers section under Main → Identity and create a new Service Provider.
-
Edit the created Service Provider:
-
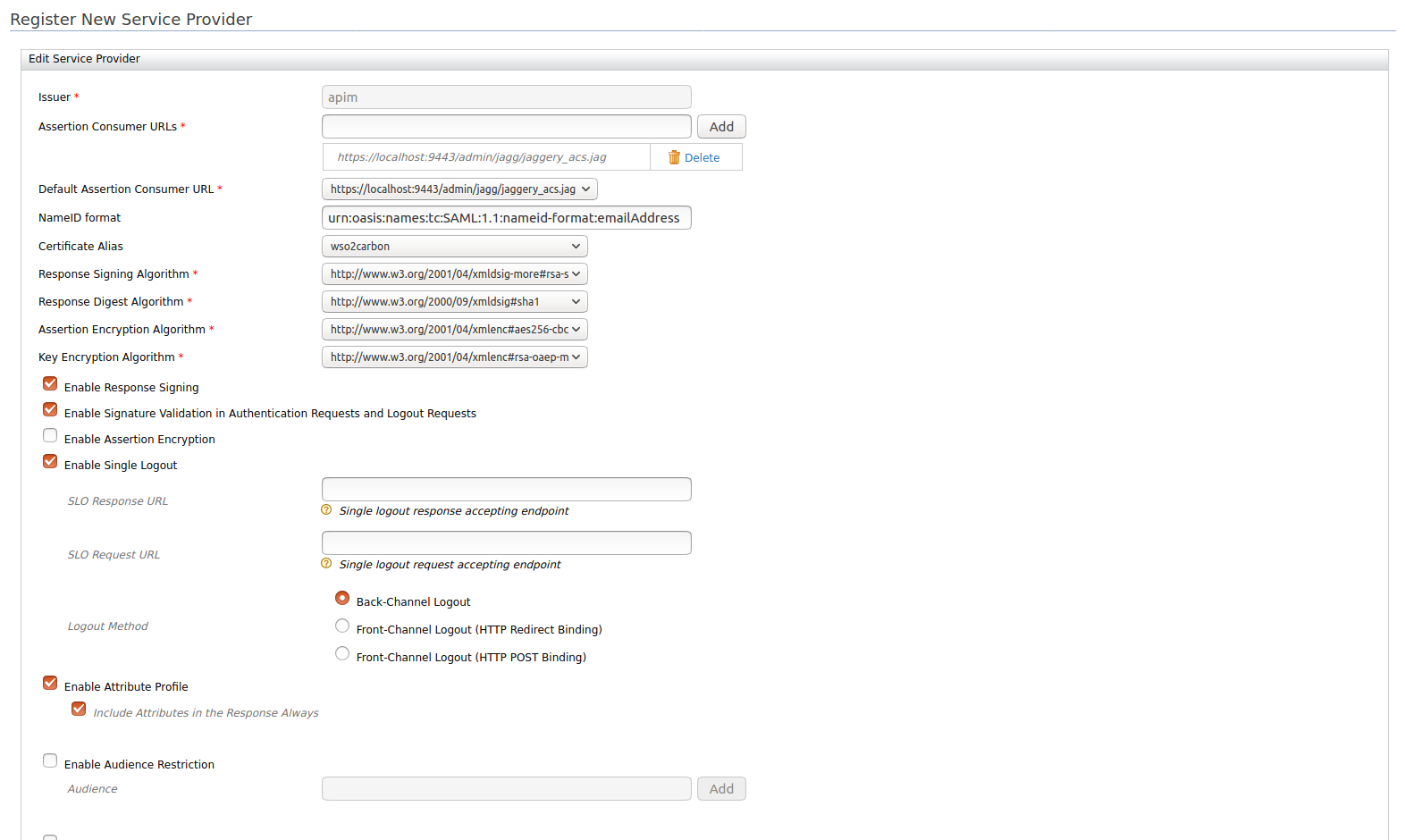
Expand the Inbound Authentication Configuration section and configure SAML2 Web SSO Configuration by providing the following information:
Issuer Specify the Issuer Assertion Consumer URLs https://{apim-ip}:9443/commonauthResponse Signing Algorithm http://www.w3.org/2001/04/xmldsig-more#rsa-sha256Enable Response Signing true Enable Signature Validation in Authentication Requests and Logout Requests true Enable Single Logout true Enable Attribute Profile true Include Attributes in the Response Always true The following image shows the sample values for SAML2 Web SSO configuration:
-
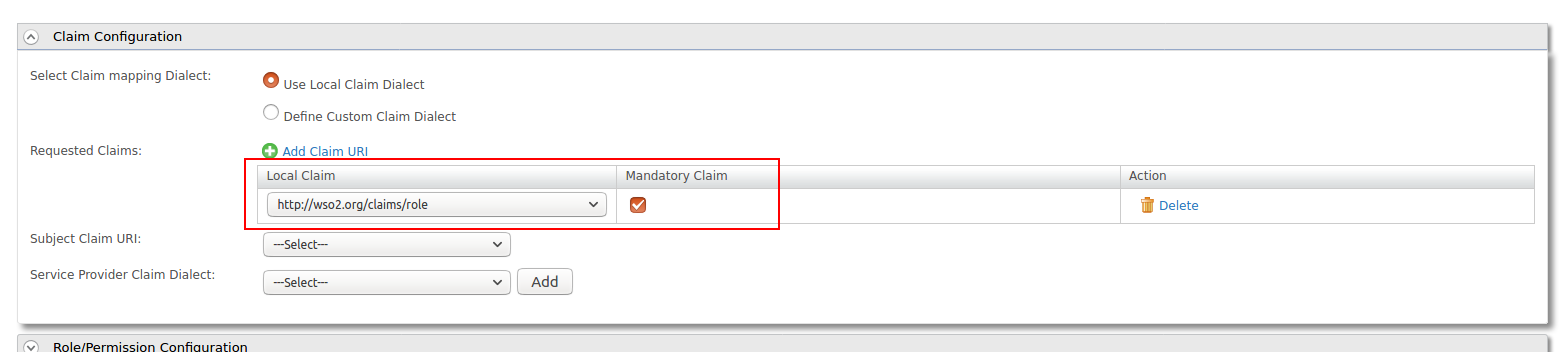
Expand the Claim Configuration section and add http://wso2.org/claims/role as a mandatory claim.
-
Update the Service Provider configurations.
In multi-tenanted environments
Carry out the instruction given below for all the tenants to be able to sign in to the API-M Web applications in a multi-tenanted environment.
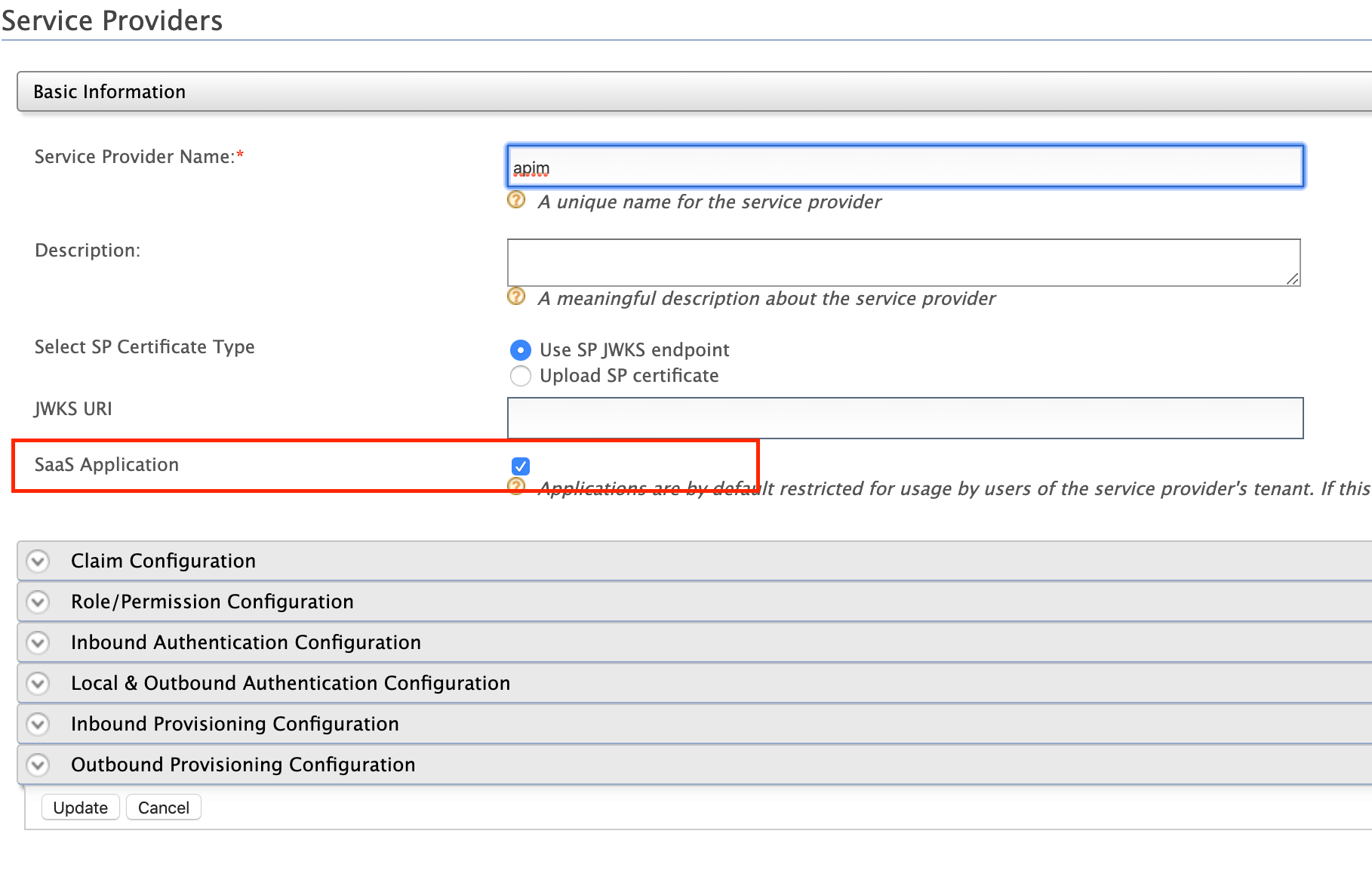
- Click the SaaS Application option that appears after registering the Service Provider.
If you do not select the SaaS Application option, only users in the current tenant domain will be allowed to sign in to the portals. You will need to register separate Service Providers for portals from each tenant.
-
-
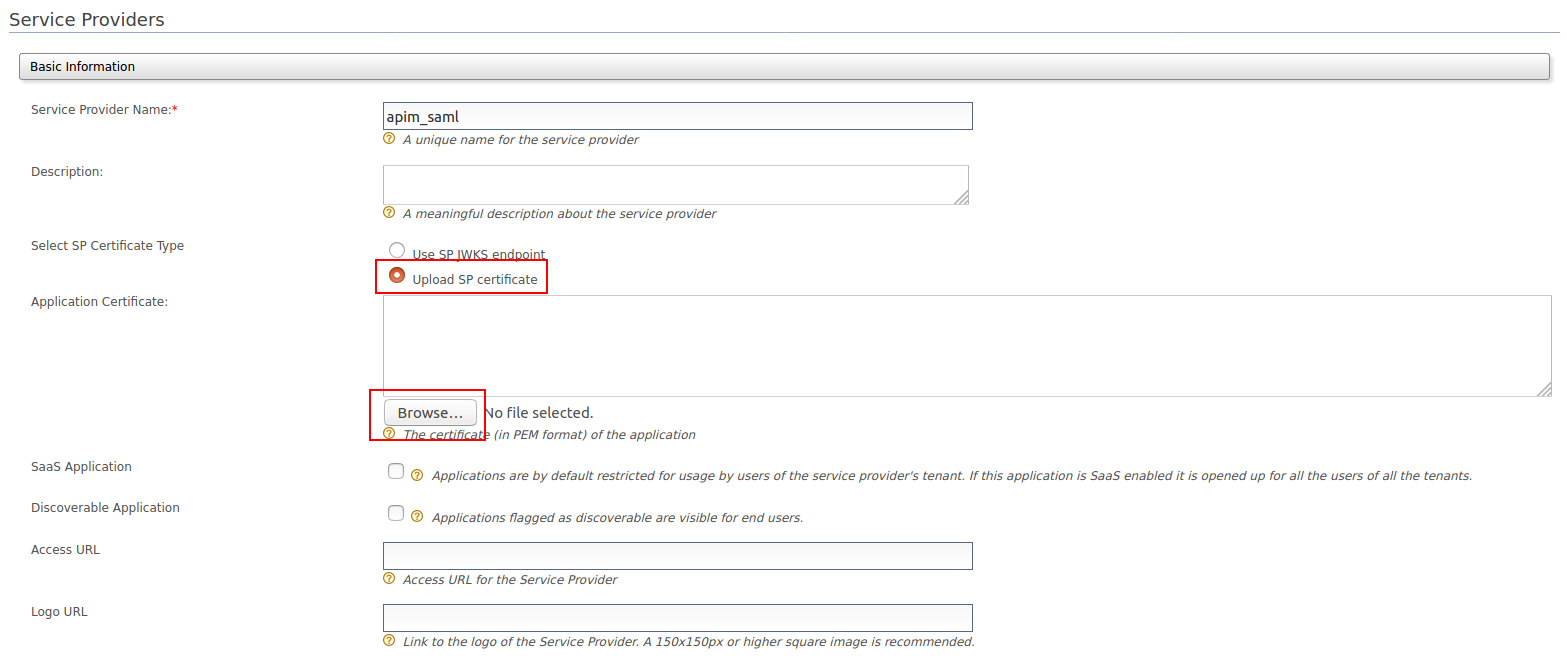
Upload the public certificate of the API Manager by selecting Select SP Certificate Type.
Step 1.2 - Create users and roles¶
-
Create the required users and roles in Identity Server. Let's assume that the following users are created in Identity Servers with the given roles.
User Role api_publisher publisher_role api_user user_role
Step 2 - Configure WSO2 API Manager¶
Step 2.1 - Configure the Identity Provider¶
-
Sign in to the Management Console of WSO2 API Manager.
https://{apim-ip}:9443/carbon -
Navigate to the Identity Providers section under Main → Identity and create a new Identity Provider.
-
Upload the public certificate of Identity Server under the Upload IDP certificate.
-
Expand the Federated Authenticators section and add the following configurations under SAML2 Web SSO Configurations:
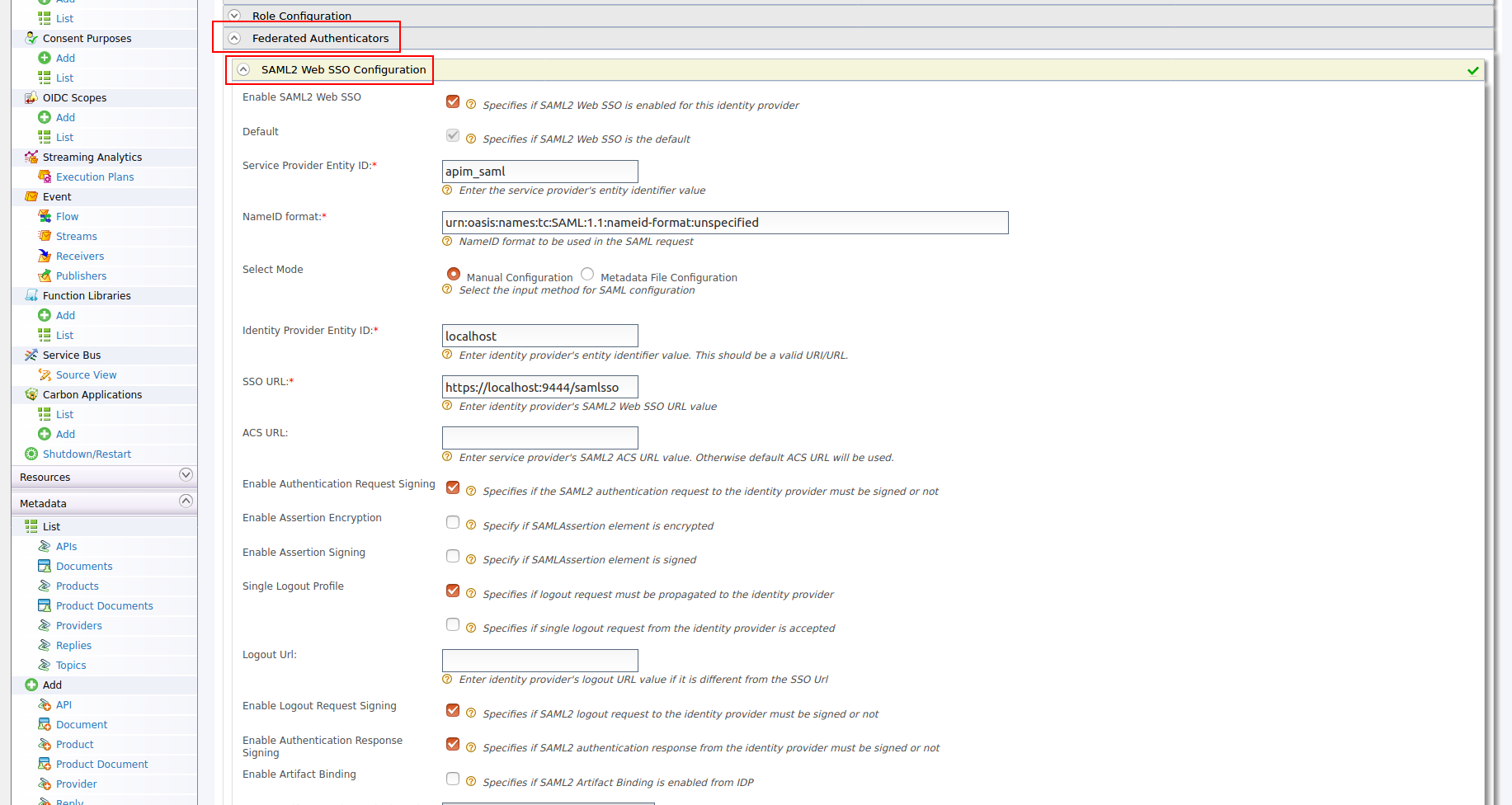
Enable SAML2 Web SSO true Service Provider Entity ID It depends on the Issuer value defined in the Service Provider configured in Identity Server above Identity Provider Entity ID localhost SSO URL https://{is-ip}:9444/samlsso Signature Algorithm RSA with SHA256 Single Logout profile true Enable Authentication Request Signing true Enable Authentication Response Signing true Enable Logout Request Signing true Enable Logout true The following image shows the sample values for SAML2 Web SSO configurations:
Note
Make sure your Service Provider configurations in the Identity Server and the Identity Provider configurations in API Manager reflect each other.
Example:
- If the Response Signing Algorithm in Identity Server is rsa-sha256, then the Signature Algorithm in API Manager should be RSA with SHA256.
- If you enabled Enable Single Logout in the Service Provider created in the Identity Server, then enable Single Logout Profile in the Identity Provider created in API Manager.
-
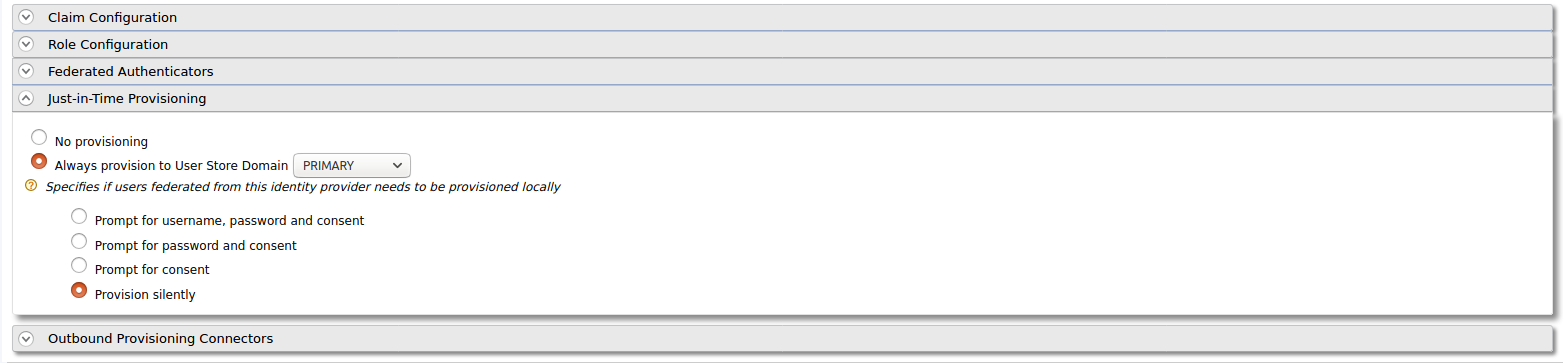
Enable Just-in-Time Provisioning to provision the users in API Manager.
-
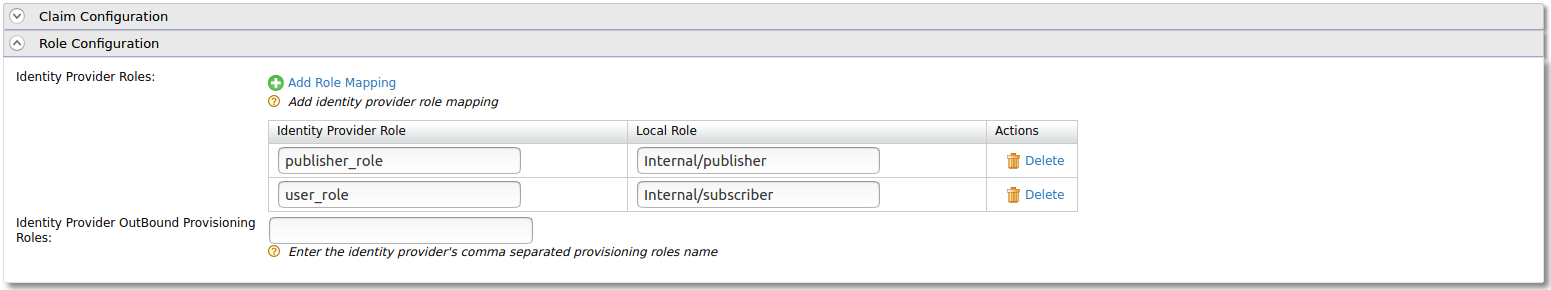
Add the following role mapping under the Role Configuration section.
Identity Server Roles Roles Mapped in API Manager user_role Internal/Subscriber publisher_role Internal/publisher Tip
Instead of using the default internal roles, you can also create new roles in API Manager and map it to the provisioned users.
Step 2.2 - Configure the Service Provider¶
-
Navigate to the Service Providers section and list the Service Providers.
There are two service providers created for Publisher portal and Developer portal named as
apim_publisherandapim_devportal. Edit theapim_publisherService Provider.Attention
You will have to log into the Developer Portal and Publisher at least once for the two Service Providers to appear as it is created during first login.
-
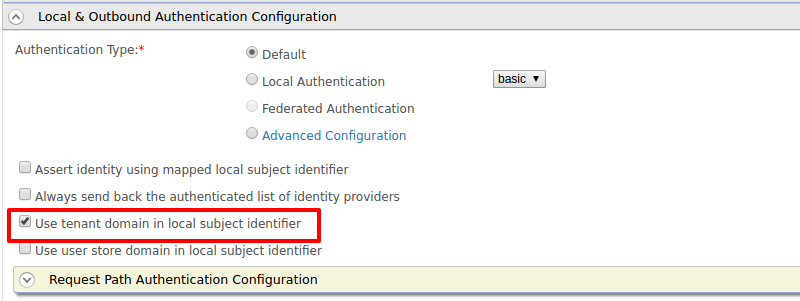
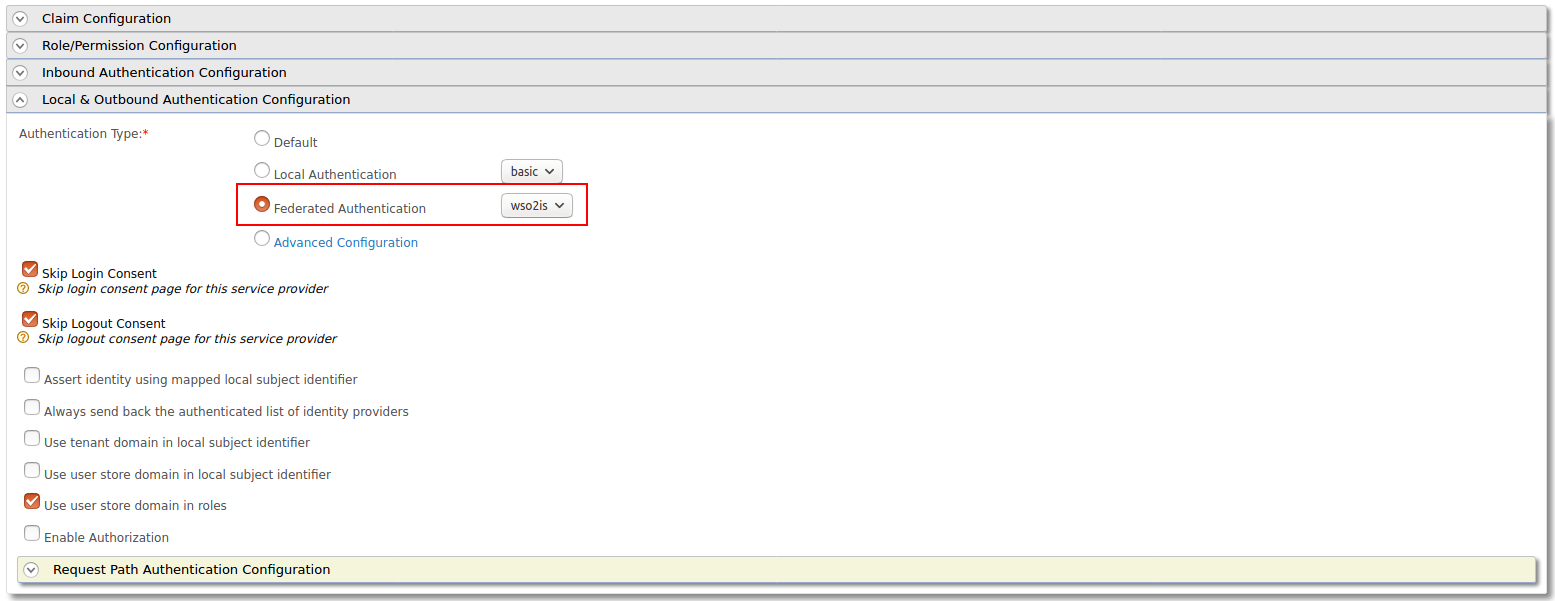
Expand the Local & Outbound Authentication Configuration section, select Federated Authentication as Authentication Type, and select the name of the Identity Provider you created and update.
-
Repeat the same step for the
apim_devportalService Provider as well.
Now you will be able to sign in to Publisher and Developer Portal using the users in WSO2 Identity Server.
Info
To learn more about Single Sign-On with WSO2 Identity Server, see SAML 2.0 Web SSO in the WSO2 Identity Server documentation.
-