Securing APIs with Mutual SSL¶
In contrast to the usual one-way SSL authentication where a client verifies the identity of the server, in mutual SSL the server validates the identity of the client so that both parties trust each other. This builds a system that has very tight security and avoids any requests made to the client to provide the username/password, as long as the server is aware of the certificates that belong to the client.
This section explains as to how APIs in WSO2 API Manager can be secured using mutual SSL in addition to OAuth2.
Create an API Secured with Mutual SSL¶
- Create an API.
- Click Runtime Configurations.
-
Click Add Certificate to upload a new client certificate.
Note
This feature currently supports only the
.crtformat for certificates.If you need to use a certificate in any other format, you can convert it using a standard tool before uploading it.
-
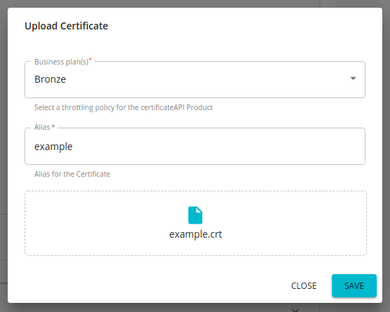
Provide an alias and public certificate. Select the tier that should be used to throttle out the calls using this particular client certificate and click Upload.
-
Save the API
Invoke an API secured with Mutual SSL using Postman¶
-
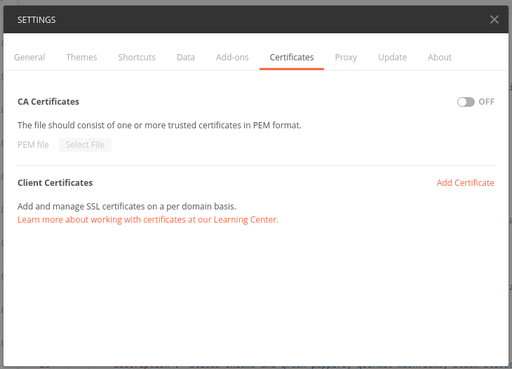
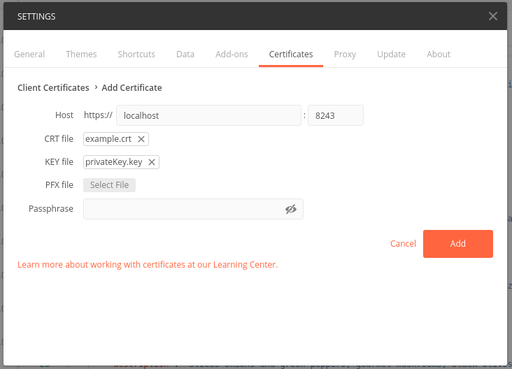
Import the certificate and private key to Postman.
-
Invoke the API from Postman.
Limitations¶
Listed below are the known limitations for this feature.
-
Application subscription is not permitted for APIs that are only protected with Mutual SSL. Therefore, subscription/application-level throttling is not applicable to these types of APIs.
-
Resource-level throttling is not applicable to the APIs that are only protected with Mutual SSL.
-
Resource-level security will not be applicable to the APIs that are only protected with Mutual SSL.
-
Scope-level security will not be applicable to the APIs that are only protected with Mutual SSL.
Handling MTLS when SSL is terminated by the loadbalancer/reverse proxy.¶
When SSL Termination of API requests happens at the loadbalancer/reverse proxy, the following prerequisites need to be met from the load balancer.
- Terminate the mutual SSL connection from client
- Pass the client SSL certificate to the Gateway in an HTTP Header. (e.g., https://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_client_certificate)
The following diagram shows how MutualSSL works in such an environment.

Using MTLS Header to invoke APIs secured with Mutual SSL¶
By default, the WSO2 API Manager retrieves the client certificate from the X-WSO2-CLIENT-CERTIFICATE HTTP header.
Follow the instructions below to change the header:
- Navigate to the
<API-M_HOME>/repository/conf/deployment.tomlfile. -
Configure the certificate_header under the [apimgt.mutual_ssl] configuration.
[apimgt.mutual_ssl] certificate_header = "<Header Name>" # This property needs to be true if the MutualSSL connection is established between the load balancer and the Gateway. enable_client_validation = false #This property needs to be true if the certificate should be decoded when it is passed from the load balancer to the Gateway. client_certificate_encode = false[apimgt.mutual_ssl] certificate_header = "SSL-CLIENT-CERT" enable_client_validation = false client_certificate_encode = false -
Start the Server.
-
Invoke the API with the custom header.
curl -k --location -X GET "<API_URL>" -H "accept: application/json" -H "Authorization: Bearer <access-token>" -H "<MTSL_Header_name>:<Certificate_Key>"
Note
The MTLS flow described above uses the Nginx load balancer. When using a different ELB to configure the MTSL with SSL termination, refer the service provider's documentation and feature catalog to do the necessary configurations.